#3911
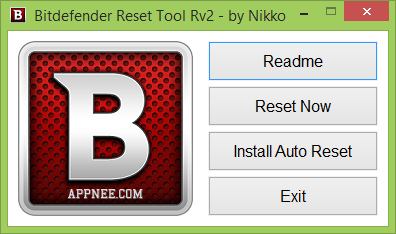
Bitdefender Reset Tool is an efficient and frequently-used automatic activation tool (solution), universal for Bitdefender all security products, compatible with all Windows OS (both 32-bit and 64-bit).
Loading...
Loading...
Loading...
Loading...
#3909
The assembly language is actually a strongly functional programming language, which can utilize all features of computer hardware and directly control them. As a machine language, corresponding to the high-level language compiler, assembly language also needs a assembler to compile its source code into executable machine code. As far as I know, there are at least two skills can not do anything without the basic knowledge of assembly language, they are reverse engineering (software cracking) and disk repair.

Loading...
Loading...
Loading...
Loading...
Loading...
#3908

Unity Game Development in 24 Hours, Second Edition may be currently the best tutorial book written for absolute beginners to the Unity game engine who want to learn it from scratch and step by step.
Loading...
Loading...
Loading...
#3907
In 2010, I mistakenly chose one of partitions on my mobile hard drive when I was using Ghost backup file (GHO) to recovery the system partition (C volume), which led to a devastating partition-level of data loss. Since then, I have been sealing this entire hard disk all the time. Until 2017's first half, I finally had enough time and patience to restore most of the data inside. And among these recovered files, I accidentally discovered a very handy and practical software - 5D PDF Creator, which was published as early as 2008, and has been discontinued and gone from Internet for many years.

Loading...
Loading...
Loading...
Loading...
Loading...
#3906

When you make real-time operation demonstrations on computer through a projector or a large screen, you may encounter such awkward situation: Because the mouse pointer is too small, no audience can see it or at least it's difficult to notice its precise location, even a bit hard to find where it is for yourself - you have to locate it depending on moving the mouse. In cases like this, PointerStick can completely solve your problem.
Loading...
Loading...
Loading...
#3905
Google SketchUp is an extremely popular and user-friendly 3D modeling tool, which is production process of design scheme oriented, and mainly used in the architectural design and relevant fields. Its creation process not only can directly express the designer's idea, also fully meet the needs of communicating with customers in time. Applying it to game design is a relatively new field with a certain amount of challenges.

Loading...
Loading...
Loading...
#3904

Today, cars are more electronized than ever before. The "This Car Runs on Code" report published in the IEEE Spectrum journal indicated: As of 2009, a typical car already contains 100+ processors, 50+ electronic control units, 5000+ meters of cabling and 100 millions of lines of code. That means, along with the more and more close integration between computer systems and vehicles, the security audit is also becoming increasingly important and complicated.
Loading...
Loading...
#3902
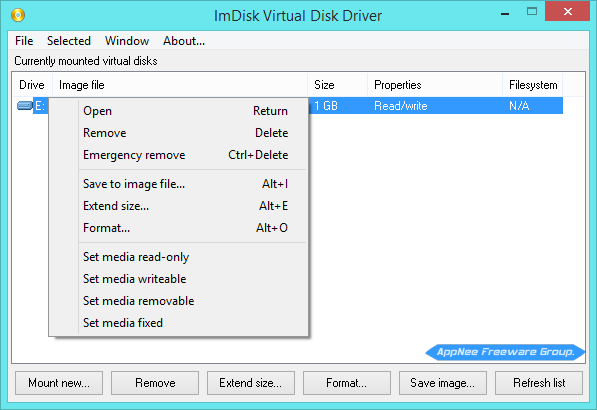
By modifying the environment variables of system or software to save a variety of commonly used temporary folders (Temp, IE Cache, Download folder, for example) to the virtual hard disk (RAM drive), we can effectively improve the file reading/writing speed and software running speed. And in fact, it can also reduce the reading/writing times of physical disk so as to prolong its service life to some extent.
Loading...
Loading...
Loading...
#3901
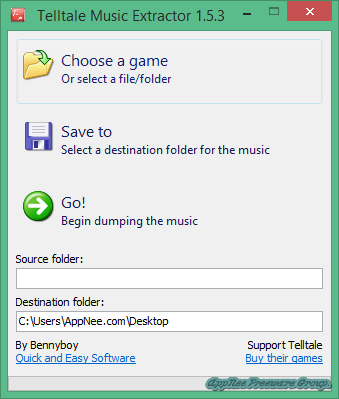
First of all, not all of the wonderful music you heard can be bought or downloaded from somewhere. Then, if I said the background music of a lot of games (especially the ones categorized in adventure type) are really awesome, I think most game players will agree. So how to get them out from games for direct play or collection? This case, third-party tools are almost always required, and of which, a game audio extractor is preferred. As for recording game music, that's just a remedy way.
Loading...
Loading...
#3900
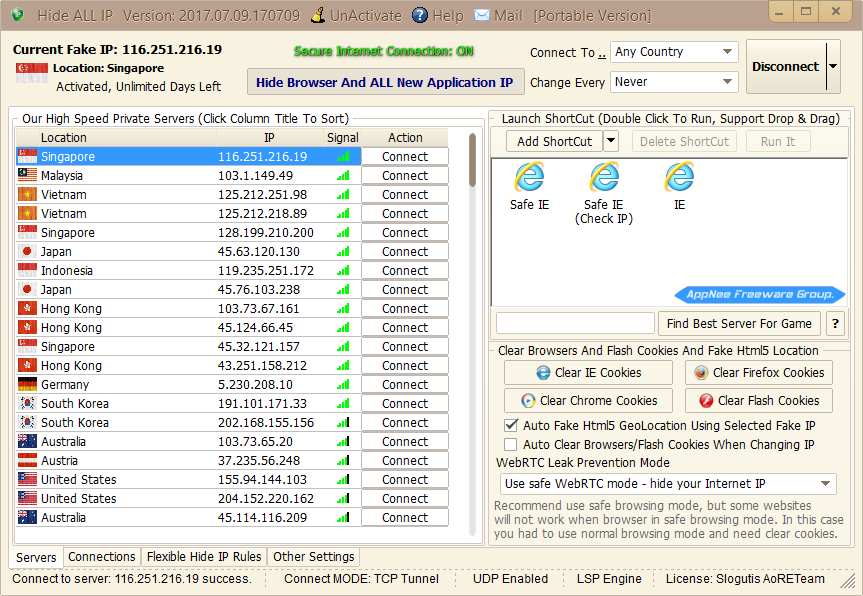
There are a lot of similar software as Hide ALL IP (their working principle is just a proxy). But to be honest, they are not very useful, or even completely useless in many countries with strict Internet censorship. Because the general HTTP/HTTPS/SOCKS5 proxies, even the so-called highly anonymous ones, almost were all blocked by the powerful network firewalls of some countries, without exception.
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...