#7082

Learning Kali Linux serves as an essential guide for cyber security enthusiasts and professionals keen on mastering the art of penetration testing and ethical hacking. It delves deep into the powerful features of Kali Linux, a distribution specifically designed for security professionals.
Loading...
Loading...
#6634
In The Ultimate Kali Linux Book, you can embark on an exhilarating adventure into the realm of Kali Linux, which is the central hub for cutting-edge penetration testing. Enhancing your pentesting abilities and exploiting vulnerabilities or conducting advanced penetration tests on both wired and wireless enterprise networks, Kali Linux empowers cybersecurity experts.

Loading...
Loading...
Loading...
#4981
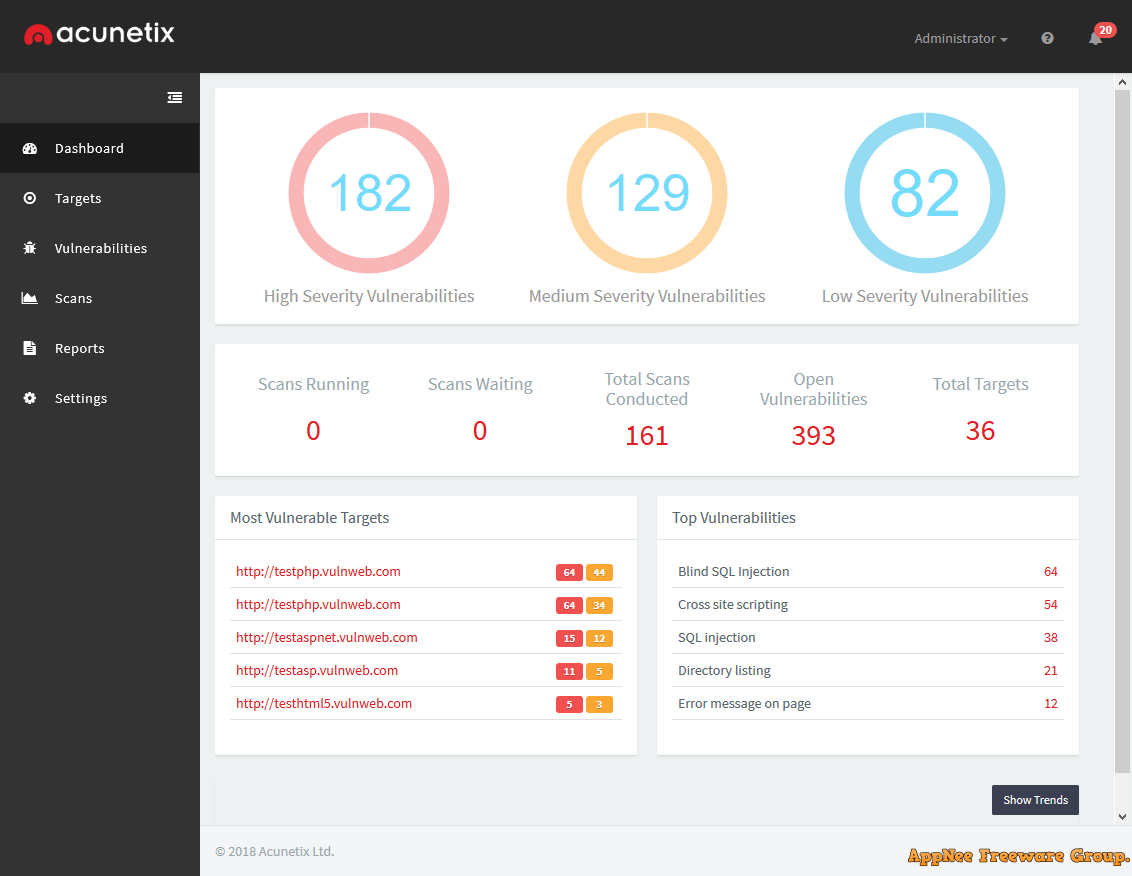
Nowadays, as many as 70 percent of websites have vulnerabilities that could lead to the theft of sensitive data of company (such as credit card information and customer info list). In particular, too many custom web applications are often not fully tested and contain a lot of undetected vulnerabilities, making them easily fall prey to hackers. There is no doubt that, the security of a website is very important, so as a website administrator, it is very necessary to conduct security penetration tests on their own servers.
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
#4793
Burp Suite (Burp for short) is a well-known and popular integrated tools platform that is used to perform security penetration tests for web applications (actually it's more commonly used for hacking activities such as web attacks), written in Java, developed by PortSwigger from United Kingdom.

Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
#4616
Kali Linux (successor of BackTrack Linux) is a free and open-source Debian-based Linux distribution funded and maintained by Offensive Security from Switzerland. Users can boot and use this OS via hard disk, live CD or live USB anytime and anywhere. Almost all open-source tools used for digital forensics, penetration testing, ethical hacking and network security assessments are included. There is no need to prepare and maintain this Linux distribution (including gathering all those software and their dependencies) by yourself, or to install any software and save any files on Kali.
Loading...
Loading...
Loading...
Loading...
Loading...
#3904
Today, cars are more electronized than ever before. The "This Car Runs on Code" report published in the IEEE Spectrum journal indicated: As of 2009, a typical car already contains 100+ processors, 50+ electronic control units, 5000+ meters of cabling and 100 millions of lines of code. That means, along with the more and more close integration between computer systems and vehicles, the security audit is also becoming increasingly important and complicated.

Loading...
Loading...
#3751

Whether you wish to be a hacker who is interested in hacking wireless network, web app, database; cracking password, software....; or want to engage in cyber security related works in the future, Offensive Security's Kali Linux (a penetration testing OS) should be always your main "battlefield" and "experimental field".
Loading...
Loading...
#3478
Two core developers of dSploit went separate ways in the fall of 2014. dSploit's father merged it into the commercial zANTI 2 with ambition to build a series of security apps on Android platform. Meanwhile, the other founder (now cSploit's father) can't wait the distant promise to open source of zANTI 2. Thus, he decided to fork the killed project and finish all the original dSploit To-Dos on a new core - cSploit, by himself.

Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
#3384

The Web Application Hacker's Handbook (WAHH for short), 2nd Edition is one of bible-level of security technology books with comprehensive, abundant and professional content highly recommended by AppNee. This second edition new added about 30% of content, mainly introduced new trends and a large number of new vulnerabilities in the field of Web security.
Loading...
Loading...
Loading...
Loading...
#2993
There are always a lot of tech news sites falsely beautify Network Spoofer and zANTI such as these tools as "one of the Android penetration testing apps". AppNee would say they were only born for hacking Wi-Fi network from an Android phone - some guys only use it for fun; but some others for illegal business deals.

Loading...
Loading...
Loading...
Loading...
Loading...