#4981
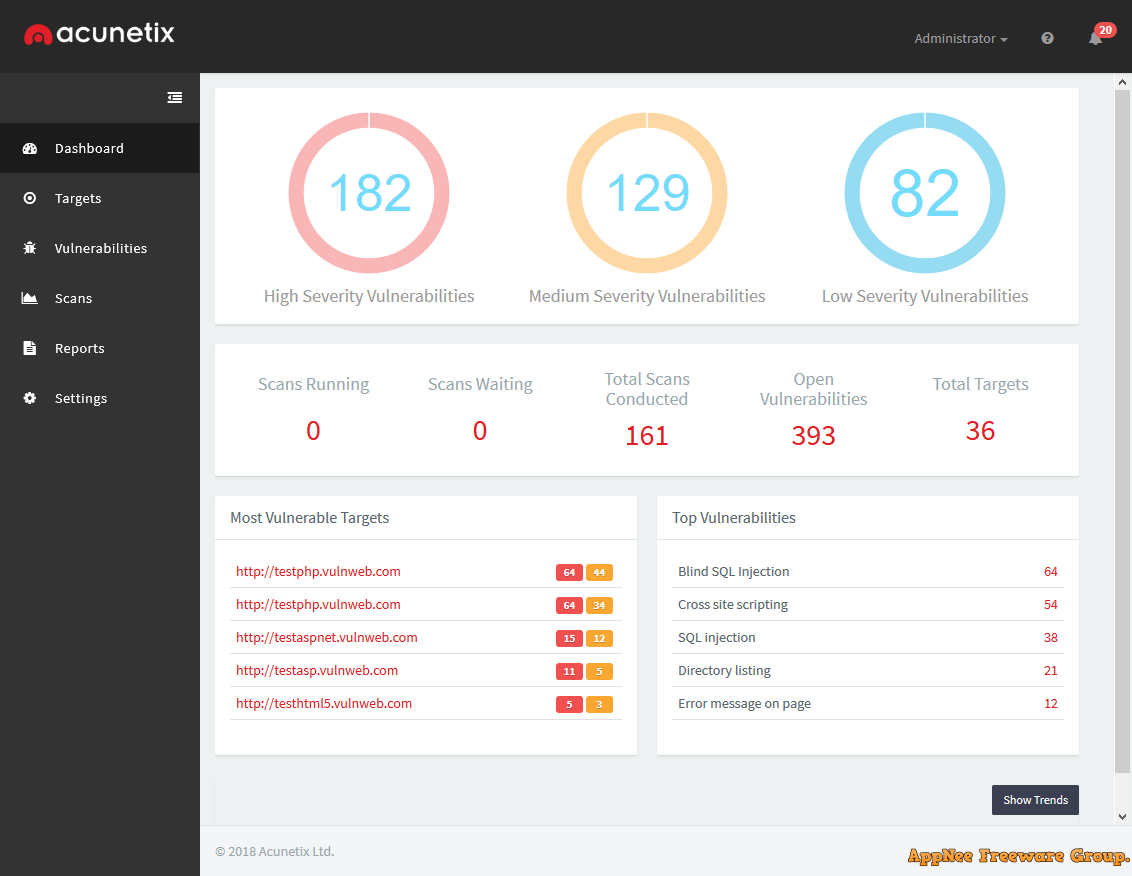
Nowadays, as many as 70 percent of websites have vulnerabilities that could lead to the theft of sensitive data of company (such as credit card information and customer info list). In particular, too many custom web applications are often not fully tested and contain a lot of undetected vulnerabilities, making them easily fall prey to hackers. There is no doubt that, the security of a website is very important, so as a website administrator, it is very necessary to conduct security penetration tests on their own servers.
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
#4425
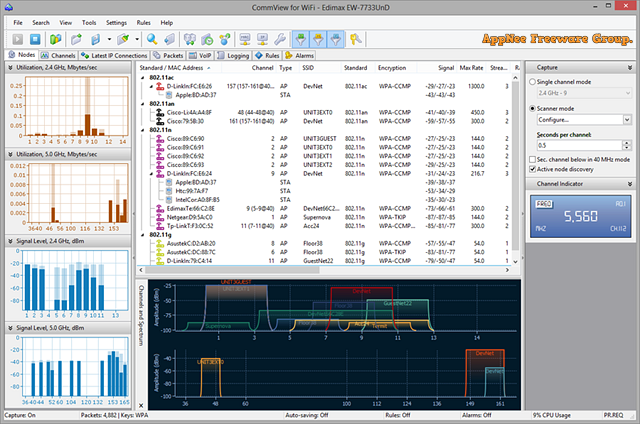
I think readers who understand wireless network well know that the security of wireless network comes with congenital deficiency - i.e.: the wireless signal is easy to leak. As a result, compared with the wired network, the monitoring action made to wireless network signals is much easier. CommView for WiFi is a powerful wireless network monitor and analyzer (i.e.: packets capturing and monitoring tool) with friendly UI, industry-leading performance, good flexibility and usability. It's specially developed (by TamoSoft from New Zealand) for wireless network administrators, security specialists, network programmers, or anyone wanting to understand the wireless network communication clearly.
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
#4270
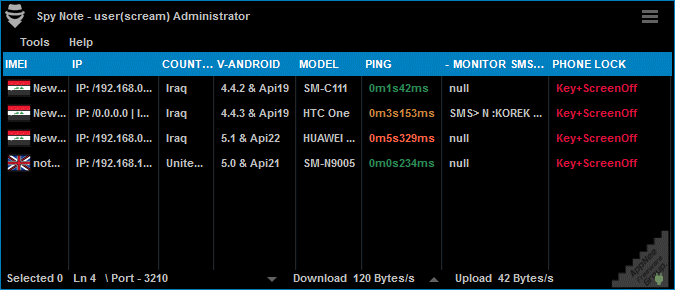
Spy Note is a free Android RAT (Remote Administration Tool/Remote Access Trojan) program developed based on Java. Its Server is written in Java, and the Client controller is written in Visual Basic .NET. After installation on an Android device, Spy Note will automatically remove its on-screen icon from victim's device.
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
#3751
Whether you wish to be a hacker who is interested in hacking wireless network, web app, database; cracking password, software....; or want to engage in cyber security related works in the future, Offensive Security's Kali Linux (a penetration testing OS) should be always your main "battlefield" and "experimental field".

Loading...
Loading...
#3478

Two core developers of dSploit went separate ways in the fall of 2014. dSploit's father merged it into the commercial zANTI 2 with ambition to build a series of security apps on Android platform. Meanwhile, the other founder (now cSploit's father) can't wait the distant promise to open source of zANTI 2. Thus, he decided to fork the killed project and finish all the original dSploit To-Dos on a new core - cSploit, by himself.
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
#3384
The Web Application Hacker's Handbook (WAHH for short), 2nd Edition is one of bible-level of security technology books with comprehensive, abundant and professional content highly recommended by AppNee. This second edition new added about 30% of content, mainly introduced new trends and a large number of new vulnerabilities in the field of Web security.

Loading...
Loading...
Loading...
Loading...
#3314

Modifying the data in memory can be not only used to decode/hack software, also used to hack all kinds of games (especially PC games and emulator based video games). Cheat Engine (CE for short) can make one game easier or more difficult, in other words, that's to be more suitable for you (but not necessarily to be more interesting)! Its principle is - the memory debugging/hacking.
Loading...
Loading...
Loading...
#3080
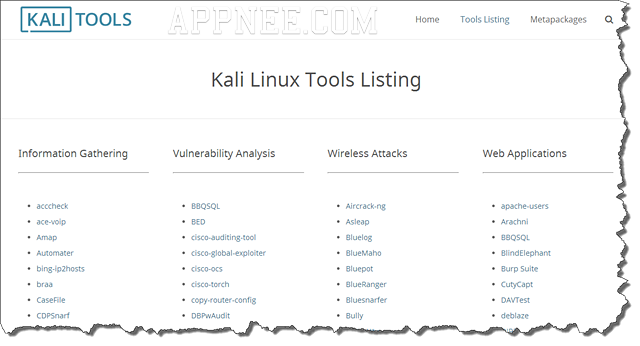
This is an official user manuals collection for all tools under Kali Linux, All documents were copied from the official site remaining all the same (color screenshots and original code format).
Loading...
Loading...
#3052

More and more critical applications have been migrated to websites now. Meanwhile, the security of these apps have become a major challenge to all kinds of institutions. Know yourself as well as the enemy, so that you can fight a hundred battles with no danger of defeat. Similarly, only by understanding the exploitable vulnerabilities exist in web applications and the attack methods adopted by web attackers, we can more effectively ensure the safety of our web apps.
Loading...
Loading...
Loading...
#2993
There are always a lot of tech news sites falsely beautify Network Spoofer and zANTI such as these tools as "one of the Android penetration testing apps". AppNee would say they were only born for hacking Wi-Fi network from an Android phone - some guys only use it for fun; but some others for illegal business deals.

Loading...
Loading...
Loading...
Loading...
Loading...