#3052

More and more critical applications have been migrated to websites now. Meanwhile, the security of these apps have become a major challenge to all kinds of institutions. Know yourself as well as the enemy, so that you can fight a hundred battles with no danger of defeat. Similarly, only by understanding the exploitable vulnerabilities exist in web applications and the attack methods adopted by web attackers, we can more effectively ensure the safety of our web apps.
Loading...
Loading...
Loading...
#2740
In fact, the features of most computer cleaner or repairer are pretty much the same, quite often the biggest difference is only the design on UI and usability. While PC Cleaner Pro's significant characteristic lies in it online database updating in real time, so it can continuously expand and improve its ability of detection and repair.

Loading...
Loading...
Loading...
Loading...
#2653

For guy who wants to be a master of network (WAN/LAN, no matter it's black, red or white), without help of various off-the-shelf classical network utilities for multipurpose uses, I'm afraid your level will stay in the DOS era of last century forever. I mean, in that case, even it was you invented the whole Internet, you could not do anything interesting or exciting.
Loading...
Loading...
Loading...
#2651
If use simple words to generalize System Explorer, AppNee gives that like this: it is the most perfect and complete alternative to the Windows built-in Task Manager. It has more detailed and authoritative system info collecting and displaying functions in expert level, but with fool-readable GUI. It's trusted and award-winning, and completely free for both personal and commercial use!
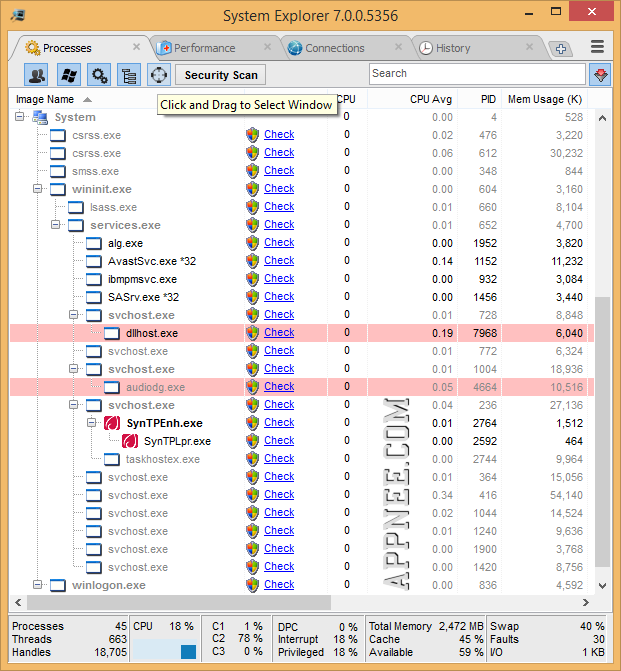
Loading...
Loading...
Loading...
#2612
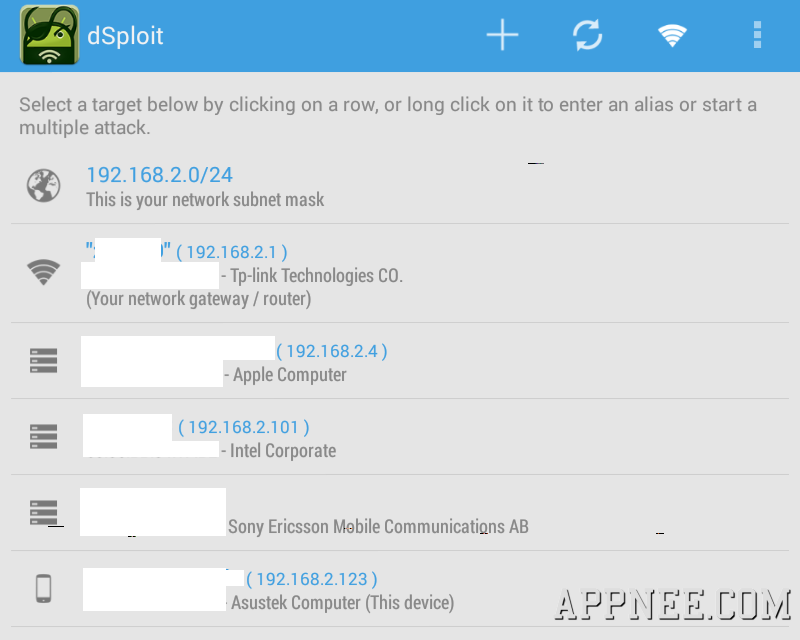
With the development of mobile devices and network, intelligent mobile phone has become a new paradise for hackers. Imagine, under this environment of everybody holds a smart phone nowadays, nothing is more active than the mobile phone viruses and the vulnerabilities' exploits of software and mobile network. Therefore, to understand and master some practical security tools seems necessary and meaningful.
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
#2591
Handbook of Applied Cryptography is one of the best, most classical cryptography books, its three authors are all the internationally well-known cryptographers and active cryptography researchers. This book contains 15 chapters (780 pages), covers all the major achievements in the development of cryptography in recent 20 years.

Loading...
Loading...
#2569

Whenever your passwords should not be written on the paper and then put under the keyboard, caught in the pages of notebook, or even just recorded on the computer with Windows Notepad... In addition, the more and more passwords will become much easier to be forgotten over time. Therefore, we need a well-designed, reassuring password managing utility.
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
#2525
Kevin Mitnick is referred to as "The world's first-rate hacker", his legendary life and hacking experience have become topic that industry and major news media take delight in talking about. Of course the present Mitnick (gave up evil and returned to good) has become the world's famous white hat hacker, he uses his own experience to guide the well-known enterprises and organizations to enhance their safety and protection measures.

Loading...
#2469

This computer security book on cryptography was published in 1995, but never hence miss such a classic work - because even in today 2015, it is still working. If you want to study cryptography, then do read Applied Cryptography written by Bruce Schneier.
Loading...
Loading...
#2438
PHP has become one of the world's most popular web programming languages from a tool used for producing personal web page. It ensures the operation of so many busiest websites on the Internet. This also brings the problems to be focused on, that's performance, maintainability, testability, reliability and the most important thing - security.

Loading...
Loading...
Loading...