#2744

Today, wireless network has got very extensive application because of its convenient use and structure, and will eventually cover every corner on the earth, I believe. But due to its broadcast form of data transmission in a wireless network environment, that will inevitably lead to security issues. Of course we can ensure data security by setting different encryption methods in a wireless router, but some loopholes of Wi-Fi network or the router itself can often make every trained hacker be able to crack/hack it.
Loading...
Loading...
Loading...
#2612
With the development of mobile devices and network, intelligent mobile phone has become a new paradise for hackers. Imagine, under this environment of everybody holds a smart phone nowadays, nothing is more active than the mobile phone viruses and the vulnerabilities' exploits of software and mobile network. Therefore, to understand and master some practical security tools seems necessary and meaningful.
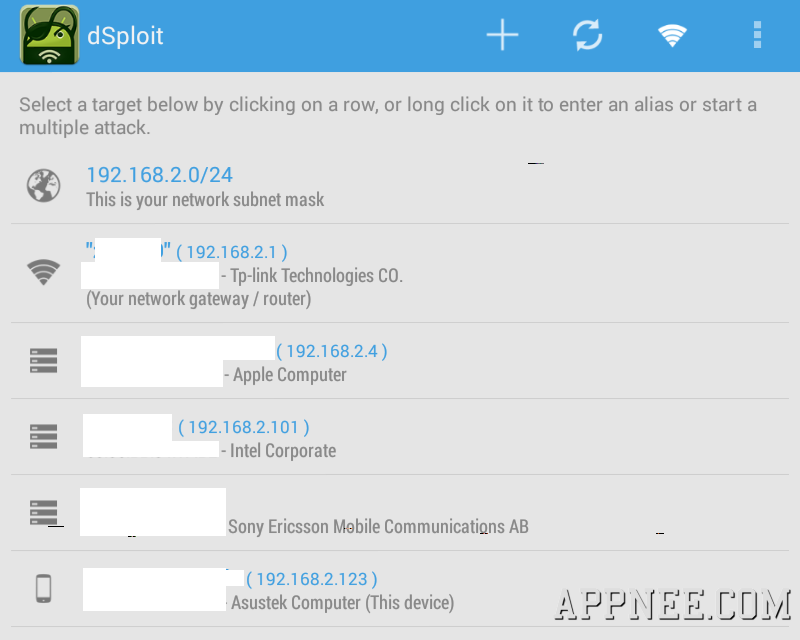
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
#2264

Kali Linux is a comprehensive platform for penetration test and security audit, has a wide range of usages in the information security industry. It comes with many advanced tools that can be used to identify the target and detect, exploit the vulnerabilities that have not been discovered in the target network.
Loading...
Loading...
#2214
About Kali Linux, if you previously used or knew about BackTrack Linux series, then I will simply say, Kali is the upgrading product of BackTrack. From Kali, BackTrack will become history.

Loading...
Loading...