#6634

In The Ultimate Kali Linux Book, you can embark on an exhilarating adventure into the realm of Kali Linux, which is the central hub for cutting-edge penetration testing. Enhancing your pentesting abilities and exploiting vulnerabilities or conducting advanced penetration tests on both wired and wireless enterprise networks, Kali Linux empowers cybersecurity experts.
Loading...
Loading...
Loading...
#4981
Nowadays, as many as 70 percent of websites have vulnerabilities that could lead to the theft of sensitive data of company (such as credit card information and customer info list). In particular, too many custom web applications are often not fully tested and contain a lot of undetected vulnerabilities, making them easily fall prey to hackers. There is no doubt that, the security of a website is very important, so as a website administrator, it is very necessary to conduct security penetration tests on their own servers.
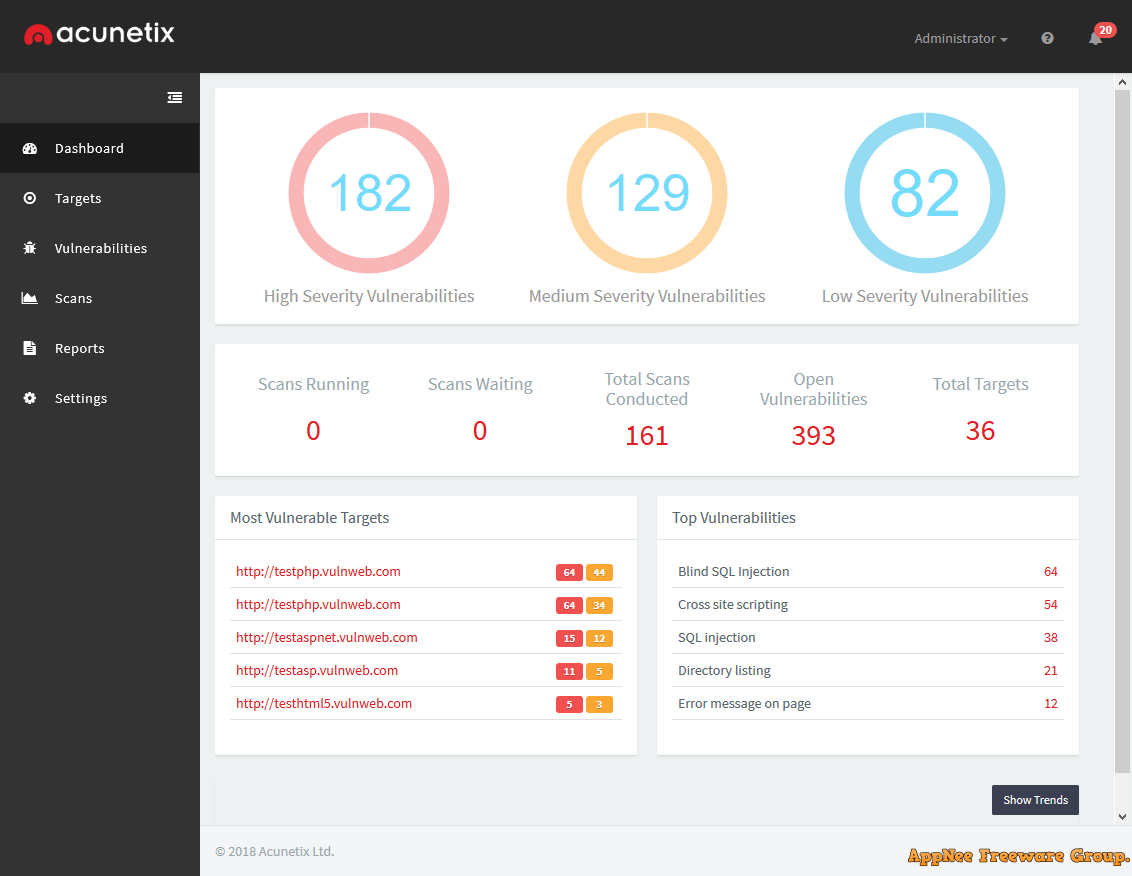
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
#4793

Burp Suite (Burp for short) is a well-known and popular integrated tools platform that is used to perform security penetration tests for web applications (actually it's more commonly used for hacking activities such as web attacks), written in Java, developed by PortSwigger from United Kingdom.
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
#3478
Two core developers of dSploit went separate ways in the fall of 2014. dSploit's father merged it into the commercial zANTI 2 with ambition to build a series of security apps on Android platform. Meanwhile, the other founder (now cSploit's father) can't wait the distant promise to open source of zANTI 2. Thus, he decided to fork the killed project and finish all the original dSploit To-Dos on a new core - cSploit, by himself.

Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
#3384

The Web Application Hacker's Handbook (WAHH for short), 2nd Edition is one of bible-level of security technology books with comprehensive, abundant and professional content highly recommended by AppNee. This second edition new added about 30% of content, mainly introduced new trends and a large number of new vulnerabilities in the field of Web security.
Loading...
Loading...
Loading...
Loading...
#3052
More and more critical applications have been migrated to websites now. Meanwhile, the security of these apps have become a major challenge to all kinds of institutions. Know yourself as well as the enemy, so that you can fight a hundred battles with no danger of defeat. Similarly, only by understanding the exploitable vulnerabilities exist in web applications and the attack methods adopted by web attackers, we can more effectively ensure the safety of our web apps.

Loading...
Loading...
Loading...
#2861

Without any doubt, Wireshark (formerly called Ethereal) is currently the world's most famous, foremost free and open source network packets capture & analysis tool. Its appearance puts an end to the future of all similar business software.
Loading...
Loading...
Loading...
Loading...
#2787
First of all, about the author of this book "Johnny Long", he has begun to research using Google to test the potential safety hazards of websites and computers as early as in 1995. What he does has developed and formed today's Google Hacking Techniques - the Google Hacking Database (GHDB) set up by him has been hosted by Exploits-DB now.

Loading...