#6805
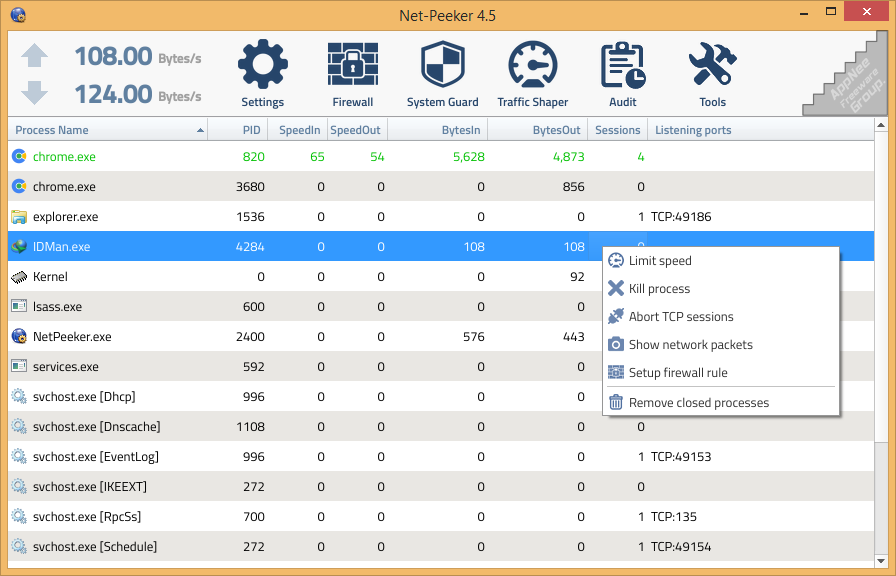
Net-Peeker (AKA: NetPeeker) is a powerful network monitoring tool that provides comprehensive insights into network traffic and activities. It allows users to monitor and analyze network performance, detect and troubleshoot network issues, and ensure optimal network security.
Loading...
Loading...
Loading...
Loading...
Loading...
#6161
Fing is a powerful and easy-to-use network security scanning tool for both PC and mobile platforms, claiming to be the #1 Network Scanner with wide acclaim in the world, developed by Overlook from Ireland. It can help you perform a variety of security checks on any WiFi network you can connect to, discover and identify all devices connected to your WiFi, test network speeds, troubleshoot network problems, and more.

Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
#6103
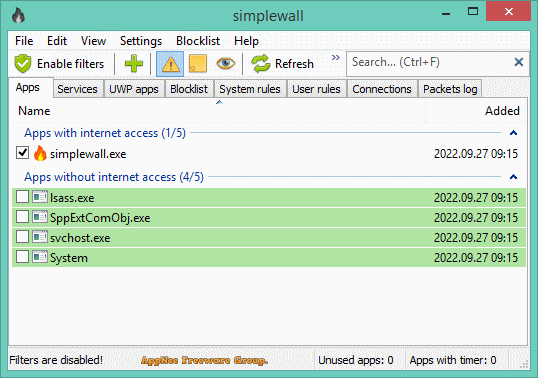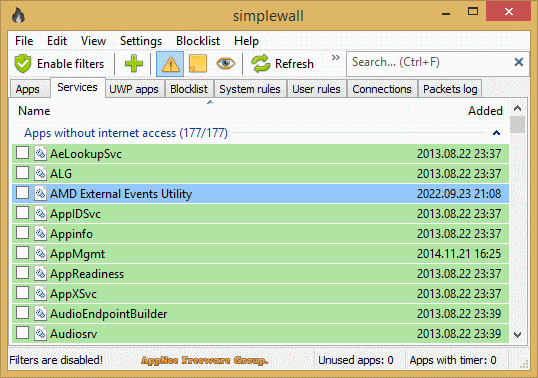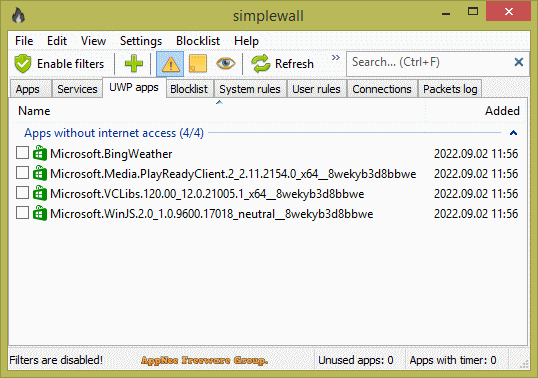
Firewall is the strongest line of defense in the system, also a barrier between the intranet and the extranet (Internet), and protects our computer by controlling the flow of packets in and out and preventing access by illegal users according to rules predefined by the system administrator. The built-in Windows Firewall is not only not powerful enough, but also difficult for the average computer users to configure and maintain (so few people use it). That's why there are many third-party firewall programs like simplewall.
Loading...
Loading...
Loading...
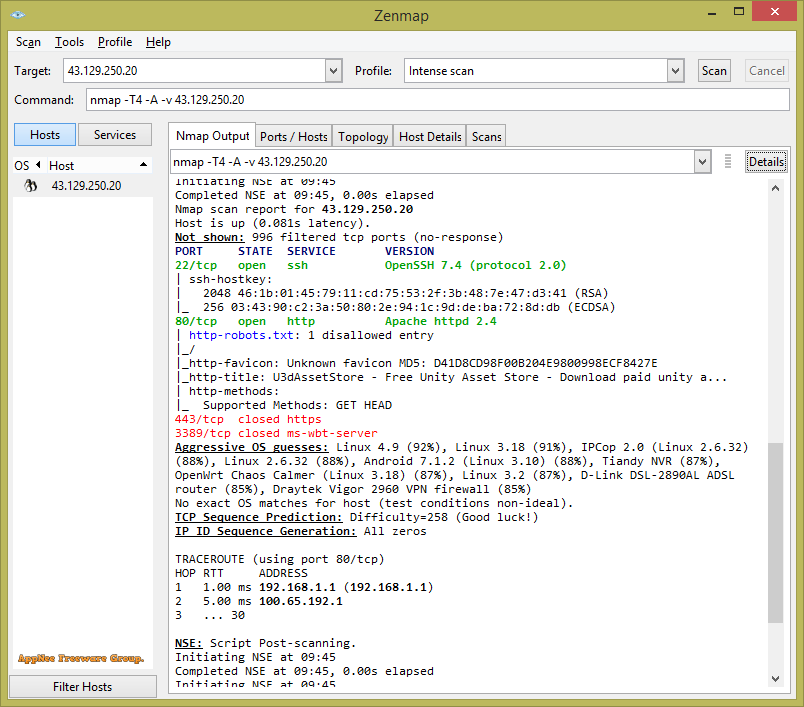
#5951
Nmap (short for Network Mapper) is a free and open-source network security scanner for large networks. It was originally developed by Gordon Lyon (Fyodor Vaskovich) for Linux in 1997, later gradually became one of the most popular network discovery and security auditing tools on multiple operating systems with the participation of many volunteers in the open source community.
Loading...
Loading...
Loading...
Loading...
#4981
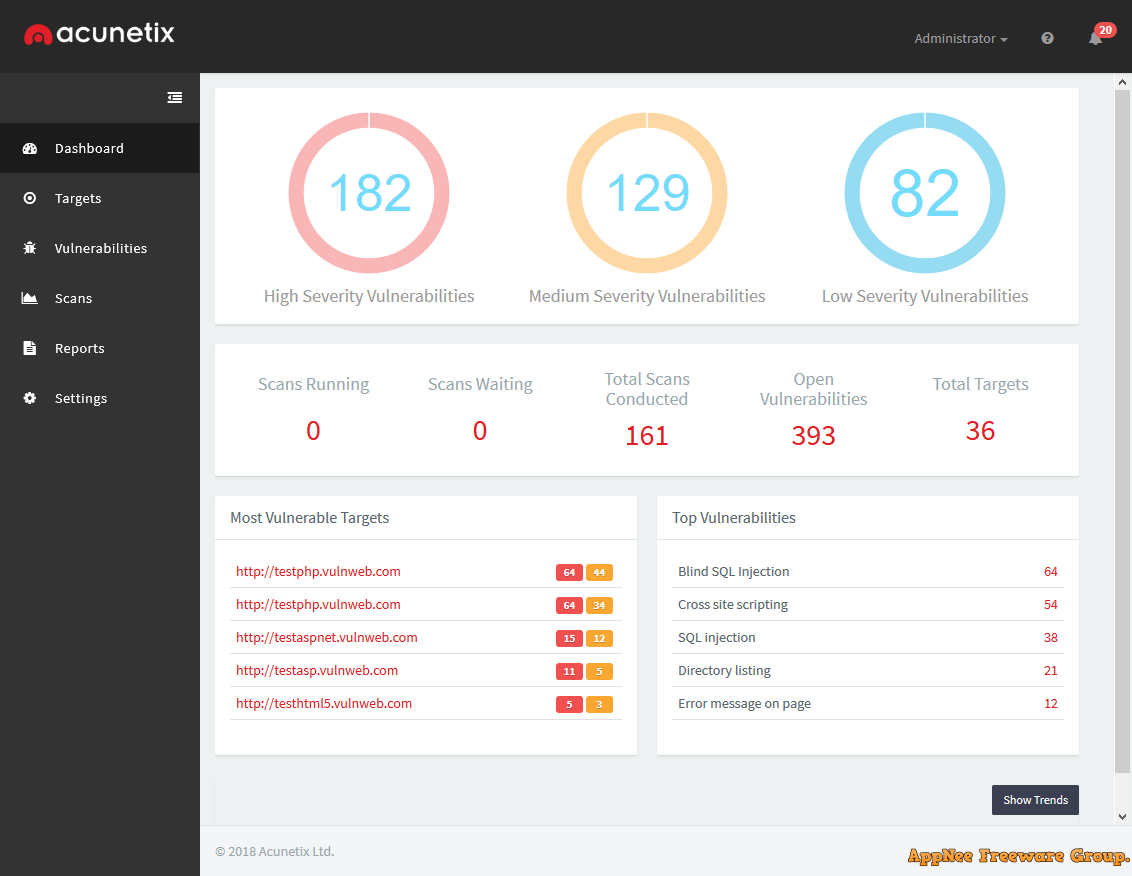
Nowadays, as many as 70 percent of websites have vulnerabilities that could lead to the theft of sensitive data of company (such as credit card information and customer info list). In particular, too many custom web applications are often not fully tested and contain a lot of undetected vulnerabilities, making them easily fall prey to hackers. There is no doubt that, the security of a website is very important, so as a website administrator, it is very necessary to conduct security penetration tests on their own servers.
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
#4616
Kali Linux (successor of BackTrack Linux) is a free and open-source Debian-based Linux distribution funded and maintained by Offensive Security from Switzerland. Users can boot and use this OS via hard disk, live CD or live USB anytime and anywhere. Almost all open-source tools used for digital forensics, penetration testing, ethical hacking and network security assessments are included. There is no need to prepare and maintain this Linux distribution (including gathering all those software and their dependencies) by yourself, or to install any software and save any files on Kali.
Loading...
Loading...
Loading...
Loading...
Loading...
#4577
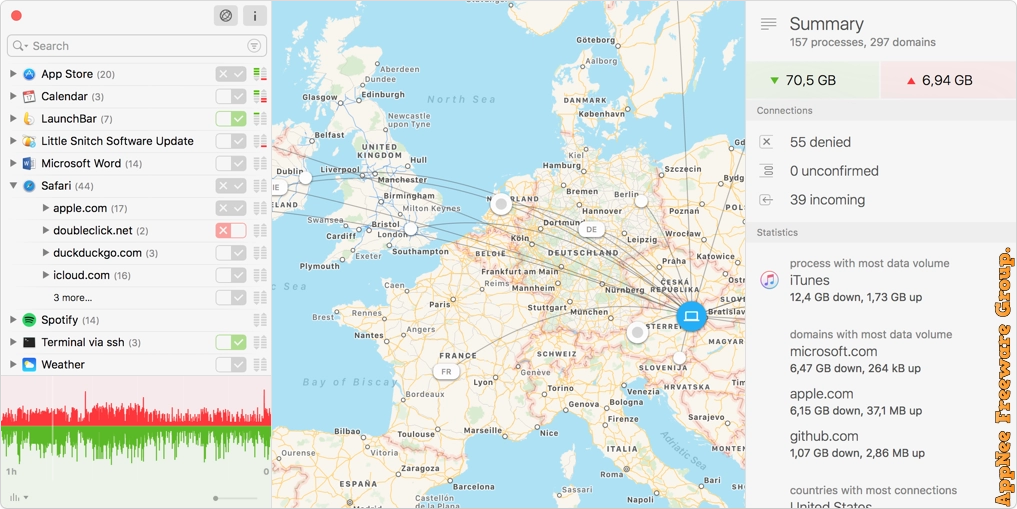
When your Mac computer is connected to the Internet, countless connections will be quietly built in the background. Once some application connects to the Internet, it can send any information that it wants to send to any place in the world. In order to monitor these connections, better maintain our privacy security, and especially withstand the tracking software, Trojans, or other types of malware, we usually have to use the boring and difficult to use firewall software. Even worse, the inbuilt firewall program of Mac OS is only able to control incoming connections, has no monitoring and controlling capabilities for outgoing connections.
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
#2745
Today, at this moment of rapid development of Internet and increasingly serious intrusion behaviors to network, the network security naturally became a focus in IT field. Accordingly, the network scanning technology has also become the most important one in this field. With help of Kali Linux OS's built-in abundant powerful network scanning tools, each guy full of passion can become network security expert.

Loading...
Loading...
Loading...
Loading...
#2598

The god knows who is using L0phtCrack as a security auditing tool to do the so-called password strength testing or recovery. I conclude that 90% of individuals are using it to violently obtain the passwords itself (through methods of dictionary, brute-force, hybrid attacks, rainbow tables, etc.). Whatever you's like to use it for, what we just can't deny is that it's the most outstanding one in similar software.
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...