#5651

It is well known that overcharging lithium batteries can seriously affect their service life, and as a direct result: the actual usable time of a fully charged battery is getting shorter and shorter. We all know this, but it's very hard to unplug the power cord when a battery is just fully charged. Because we tend to forget that our phones are charging, and we overcharge them almost every time (even put them in front of our eyes). A regular alarm clock is totally useless for this, because you can't be sure when your phone will be fully charged exactly.
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
#5650
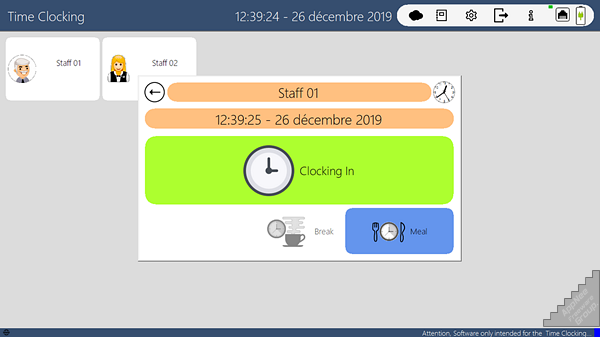
JYL Time Clock is a simple, practical personal time tracking and management tool designed for small- and medium-sized companies, developed by JYL Software from France. It can help employers/managers quickly record each employee's working time, resting time, mealtime, absenting time... It's very useful when you need to manage or track the employees/users.
Loading...
Loading...
Loading...
Loading...
#5649
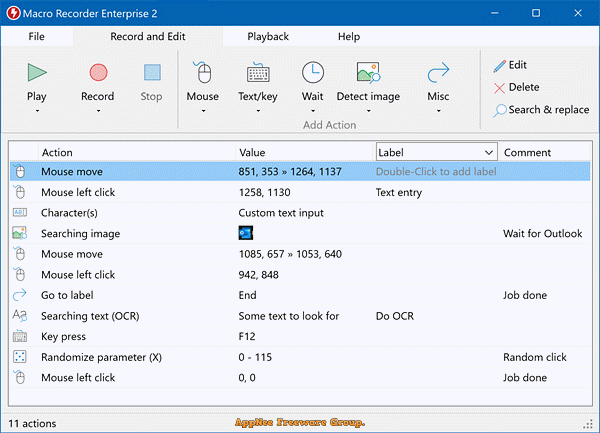
Macros can be seen as a script that consists of a sequence of instructions used to perform a specified task. There are many kinds of macros, among which keyboard and mouse macros are the most common, mainly include mouse movements, mouse clicks and keystrokes. To increase productivity and avoid repetitive tasks, using macros to automate computer operation is the most common and effective solution.
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
#5648
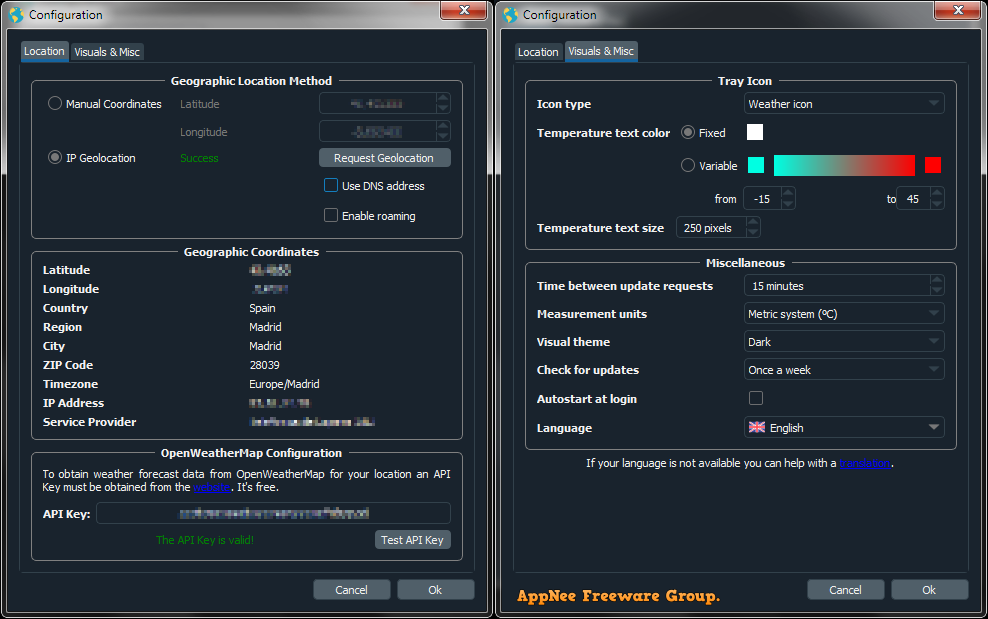
As a matter of fact, it's hard to find an overall satisfactory desktop weather application. Many weather forecasting programs known for Windows either don't offer enough or accurate weather information, or are much too bloated in file size or UI design, or even don't work at all. If you want a free, lightweight program that comes with an impressive features set, Tray Weather may be just what you are looking for.
Loading...
Loading...
Loading...
Loading...
#5647
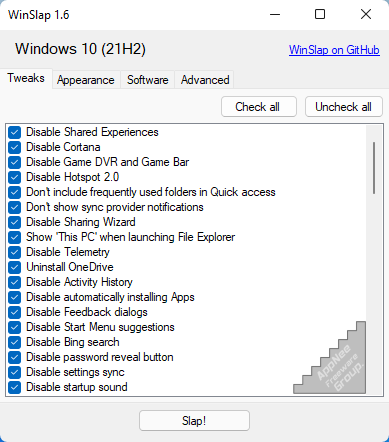
WinSlap is a free and open-source handy tool for quickly configuring a Windows 10 installation with a series of useful tweaks and settings. It was originally developed for personal use only by Sven Mauch from Germany, so there is no guarantee that it works as intended, doesn't break your system or is actively maintained.
Loading...
Loading...
Loading...
Loading...
#5646
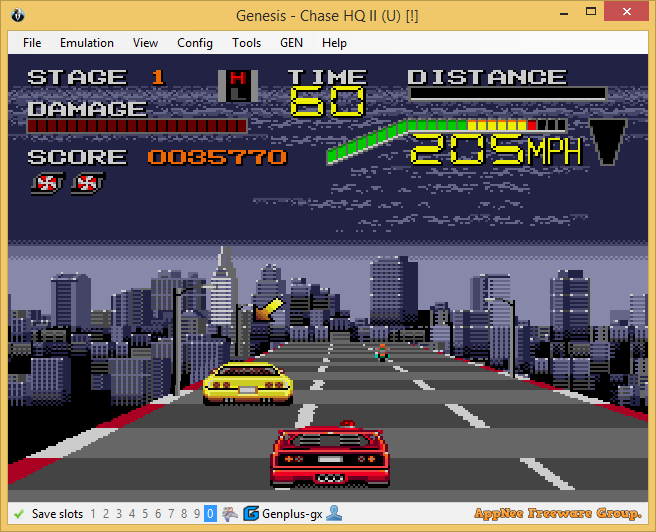
BizHawk is a free and open-source multi-system universal emulator written in C#. Its goal is to eventually simulate all game consoles, and already supports FC, MD, GBA, SFC, SMS, NES, SNES, N64, PC Engine, SS, PS, PSP, and so on more than 10 game consoles. It comes with the professional TAS functions while taking the ease of use into account. That said, BizHawk not only can be used for game clearance video production with TAS, but also is friendly for casual gaming.
Loading...
Loading...
Loading...
Loading...
#5645

There are four classic arcade games in this post: Tumblepop, Diet Go Go, Joe & Mac Returns, and Jumping Pop. The first three are all the works of Data East from Japan, were successively released in 1991, 1992 and 1994. Among them, the Joe & Mac Returns is a hybrid work of Tumblepop and Joe & Mac of Data East. The last game is a highly imitative copy of Tumblepop, was produced by ESD from South Korea and released in 2001.
Loading...
Loading...
#5643
Domain-Driven Design (DDD) teaches us how to make good software, but it also teaches us how to use the object-oriented technology. Good software should be based on domain-driven design. However, it is difficult to adopt DDD in the software development process. Even experienced developers will have a hard time finding the right way to implement DDD. In other words, DDD gives us a whole new perspective on designing software, but it also leaves developers with a big puzzle: How do you put domain-driven design into practice?

Loading...
Loading...
Loading...
#5642

As we know, the production process of software is: analysis, design, programming, testing, and deployment. In the past, the analysis and design of software were separated. As a result, the results of software requirement analysis cannot be directly designed and programmed, while the code that can be programmed and run distorts the requirements, causing customers to find that many functions are not what they want only after running the software, and the software cannot quickly follow the changes of requirements.
Loading...
Loading...
Loading...
#5641
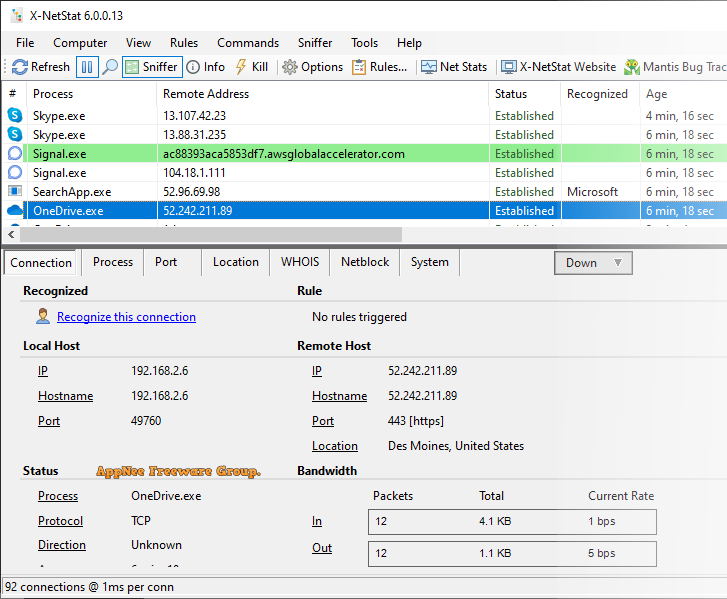
When you use your computer, whether it's checking email, chatting, browsing websites, listening to music, watching videos, playing games, or even getting hacked... Your computer has a lot of network/Internet connections in the background (whether they are authorized or not).If you want or need to get the maximum information on all your current network and Internet connections in a fairly convenient and understandable form, give X-NetStat a try.
Loading...
Loading...
Loading...
Loading...
Loading...