#4082
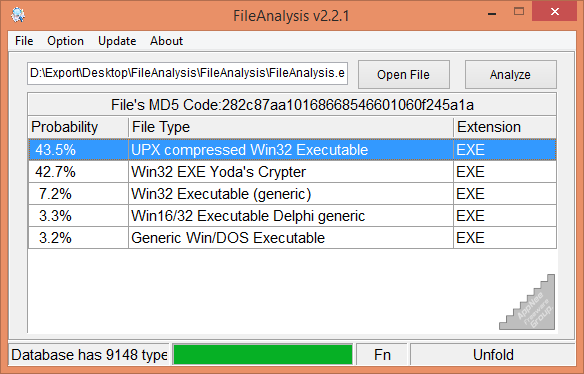
For files without an extension name, or some proprietary format of files that any common software cannot read/write, if you're sure it's a media file, then you can try using MediaInfo to detect its file metadata first. Alternatively, you can also direct use FileAnalysis to analyze its file type, thus determine that what software generated, encapsulated or encrypted this file.
Loading...
#4080
PSX Emulation Cheater (PEC for short) is a universal plugin application supporting for all kinds of PSX emulators that allows you to apply GameShark (video game cheat cartridges) cheats codes to PlayStation 1 game ROMs with these Sony PlayStation game console emulators. It is an old and discontinued software (the final version is v2002.2), but still works well now.

Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
#4079

Often someone complains that the traditional Windows logon authentication way using password is not convenient enough (especially for those PCs set up with a very complex login password), and its security is not high enough. This case, you can try Rohos Logon Key this useful tool from Moldova. It is capable of using a USB flash drive for system logon authentication. That's to say, you don't have to login Windows when it boos by inputting your password, instead, that just needs you to insert the specified USB drive.
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
#4078
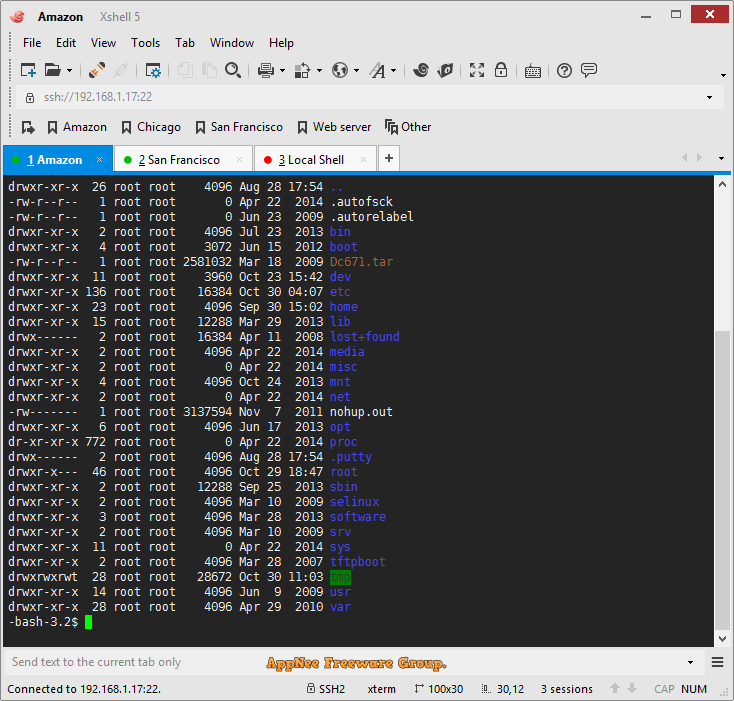
Xshell is a powerful and user-friendly terminal emulator (namely implementing the operation and management to remote hosts in a local computer) from South Korea, supports SSH1, SSH2, FTP, SFTP, Telnet, rlogin, and Serial protocols. It enables users to directly connect to the remote hosting via Internet, so as to easily control Linux servers on Windows.
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
#4075
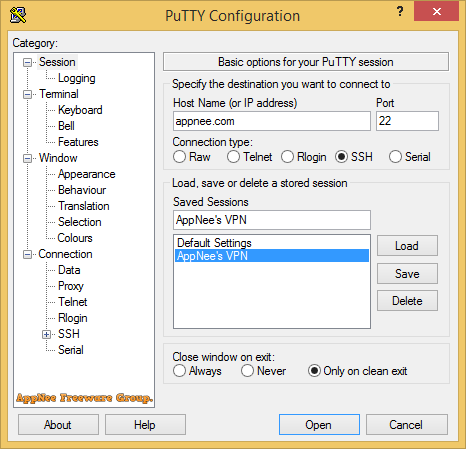
With the popularity of Linux applications on the server side, Linux system management increasingly relies on the remote control. Among various remote login tools of the same type, PuTTY absolutely deserves to be called one of the best that are very suitable for remotely administrating Linux servers by webmasters or administrators.
Loading...
Loading...
Loading...
Loading...
Loading...
#4072
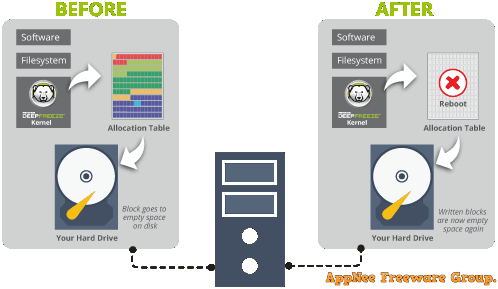
In environments that use and alter PC with high frequency (such as company PCs, school computers room, Internet cafes), it's necessary to make computer OS restore its original state at each reboot or specified time. Because compared with reinstalling and setting up the system over and over, its advantage is self-evident. This case, in addition to utilizing some hardware (PCI-E recovery card) to restore OS, your only best software solution is to use Deep Freeze such kind of reboot-to-restore tool. Its capability far surpasses programs like Returnil Virtual System and Shadow Defender.
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
#4068

CorelDRAW Graphics Suite is a very popular graphics design software with powerful and easy-to-use functions, launched by Corel Corporation from Canada for the first time in 1989. Many magazine covers, film posters, product trademarks, book illustrations... that we can see in daily life are all designed using it. Nowadays CorelDRAW Graphics Suite has become one of the must-have software together with Photoshop for most graphics designers.
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
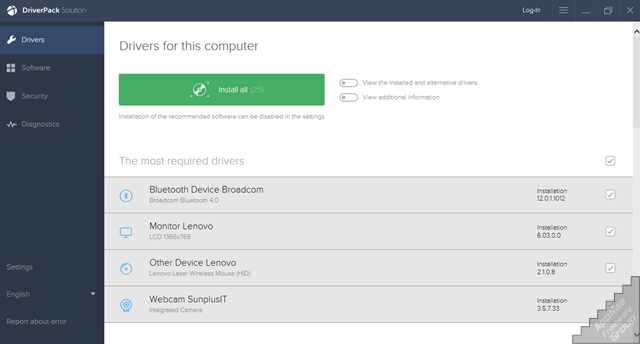
#4065
DriverPack Solution (formerly called DriverPacks) is a revolutionary free hardware drivers detecting and updating online/offline solution from Russia that applies to all hardware. Scrupulous users may see that its official website is still using the top-level domain .su (Soviet Union) in the Soviet Union era (ICANN has made many efforts to eliminate it, but always ends in failure).
Loading...
Loading...
Loading...
Loading...
Loading...
#4064
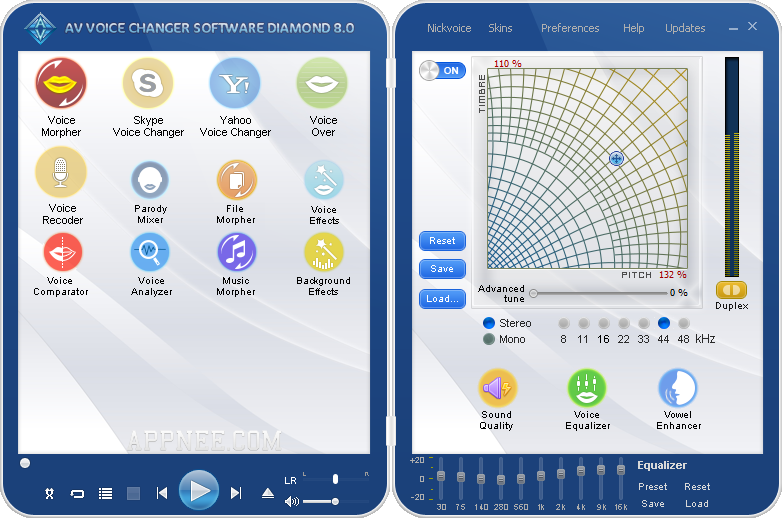
Voice/video chat is already not a new thing now. But if we could add a bit of whimsy into it, such as voice morphing, that would make the chat game more interesting. In order to achieve this effect, you may already know that the classic and famous AV Voice Changer Software can do it for us.
Loading...
Loading...
Loading...
Loading...
Loading...
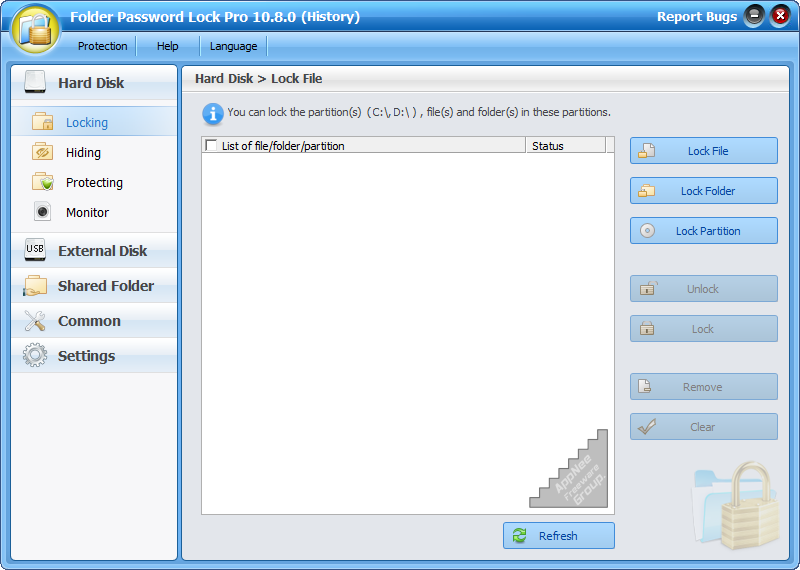
#4059
Whether on your own computer or a public one, we always have some important or privacy-related files and data that do not want others to see or get. In this case, what we can do is to use some software to protect them in primarily five ways: monitoring (passive), hiding (junior), locking (can be easily hacked by advanced computer users), password protecting (ditto), encrypting (the safest, but not convenient).
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...