#6651
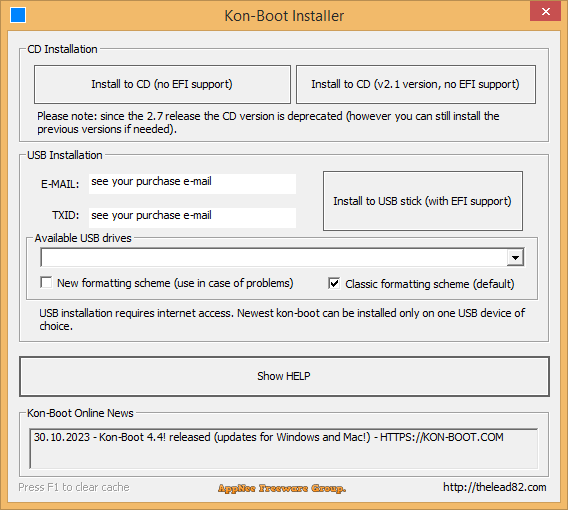
Kon-Boot (AKA: kon boot or konboot) is a powerful, professional, and popular login password bypassing rather than removing tool for Windows and Mac platforms, developed by thelead82 (LEAD82) from Poland. It enables you to access any computer even without knowing the account and password, and supports almost all versions of Windows and Mac. If you've forgotten your system password, or want to infiltrate some computers that have login passwords or even BitLocker disk encryption feature enabled, then Kon-Boot can help.
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
#6386
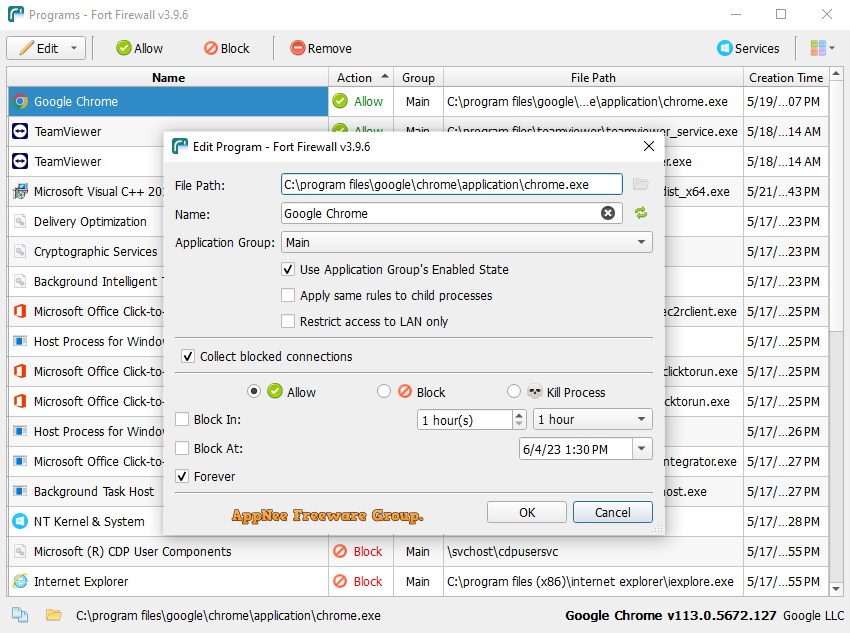
To protect the security of the computer, in addition to anti-virus software, another means is a firewall. The firewall has two main purposes: 1) To resist the attack of the external network on the local computer; 2) To effectively control the access of the local program to the Internet. It's a pity that Windows' built-in firewall has a single function and poor usability, so there are a large number of third-party firewall programs. Of course, all third-party firewalls implement corresponding functions based on the operating mechanism of Windows' built-in firewall.
Loading...
Loading...
Loading...
Loading...
#6182

When you have any problem with Windows account passwords, you don't have to try each standalone password resetting tool any more. Now, Windows Password Solutions integrates almost all popular Windows password-related tools in one place, which can bring you a lot of convenience and save you a lot of trouble.
Loading...
Loading...
#6150
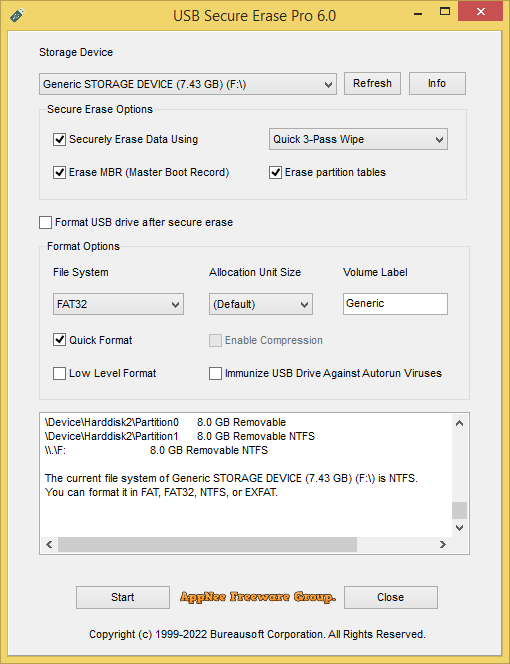
In order to erase a USB drive, some users may just delete files or format it. However, neither simple deletion nor formatting can completely erase files, because many data recovery programs can easily and quickly recover deleted or formatted files. Therefore, computer users need to be careful when discarding or selling USB drives, as a large amount of data involving personal privacy and even company secrets can be found on many recycled used flash drives.
Loading...
Loading...
Loading...
Loading...
Loading...
#6052
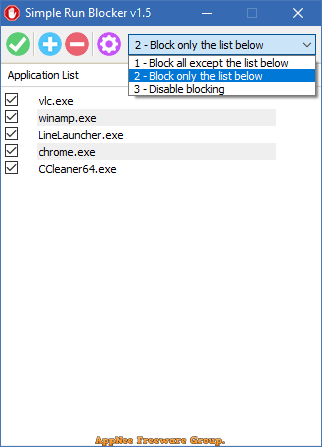
In order to prevent unauthorized people from opening some apps on our smartphone and exposing privacy, we can use the built-in or third-party app locking feature. On computer, we can use the professional AskAdmin or the more friendly Simple Run Blocker to block given programs from being run by others. For example: forbid children to open certain games or software.
Loading...
Loading...
#5956
Everyone has more or less personal privacy on his phone and computer. In order to ensure that our privacy is not leaked, we can use the app lock on mobile phone to ensure that we need to provide passwords when accessing certain apps. But on the computer side, as long as the computer is logged in, anyone can access any file and run any program on it. This may lead to the disclosure of personal privacy and important information. In this case, AskAdmin can help you.
Loading...
Loading...
Loading...
Loading...
#5801
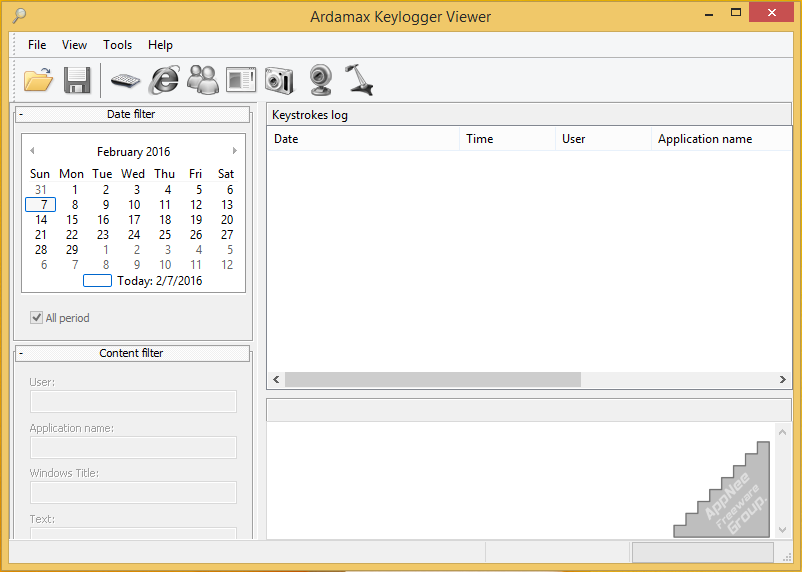
Sometimes it's necessary to keep track of the computer use for a number of reasons, like a company wants to know how its employees are doing at work, or a parent wants to know how their children are using their computers, and you want to see what others are doing on your computer after you leave. This is where software like the keylogger (keystroke logging) comes in. But you'd better not use it for illegal or unethical purposes!
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
#5684
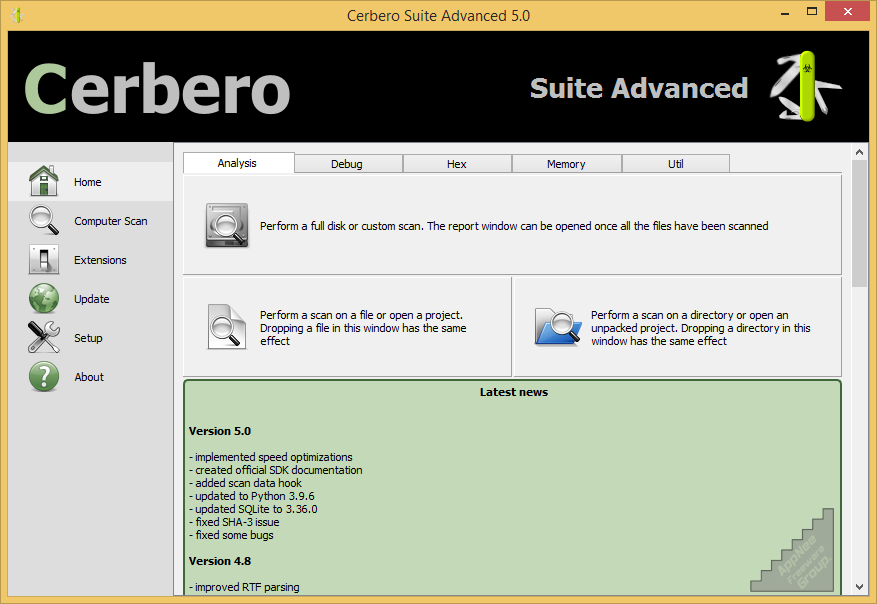
Cerbero is an advanced, professional malware classification and file security analysis tool for Windows, Mac and Linux platforms. It was designed to inspect the structure, code and many other things of dozens of file formats for reversing, malware triage, forensics or software development purpose.
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
#5620
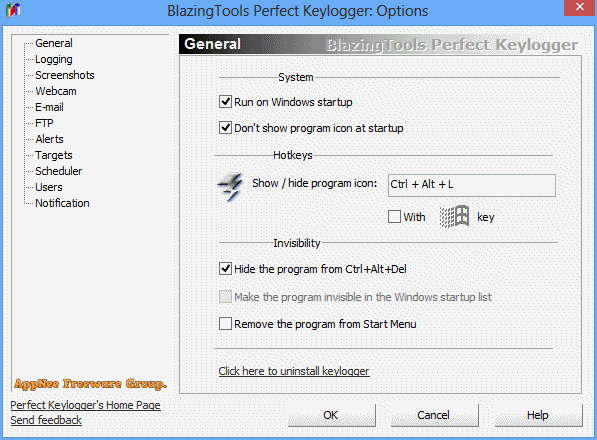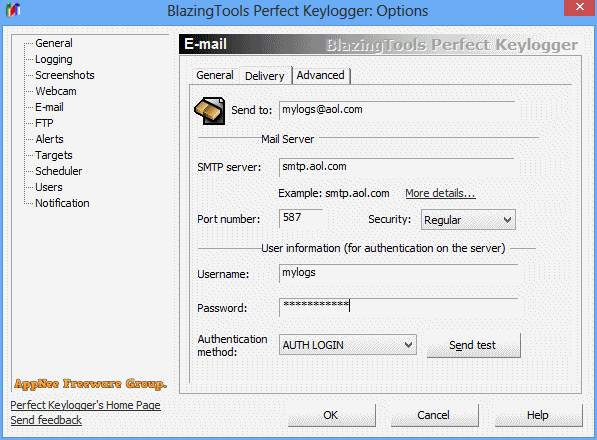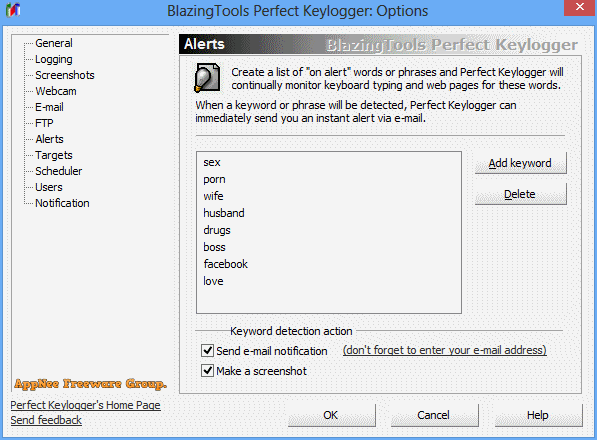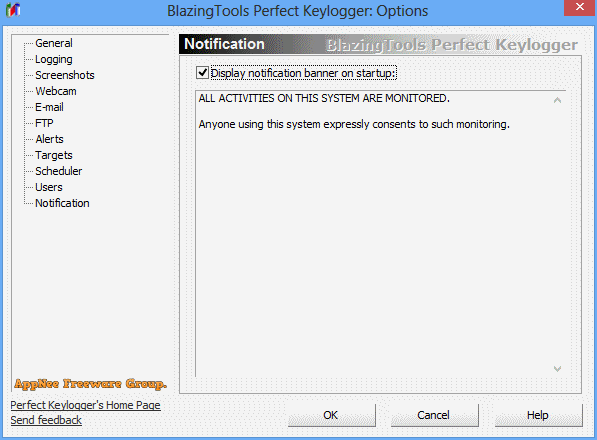
Perfect Keylogger is an excellent keyboard logger created as an alternative to the very expensive commercial products such as iSpyNOW, Spector Pro, eBlaster. It has similar functionality, but is easier to use. Because it hides the complex internal mechanisms behind a user-friendly interface. It is also the first keylogger software solution that can be completely invisible in Windows Task Manager.
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
#5515
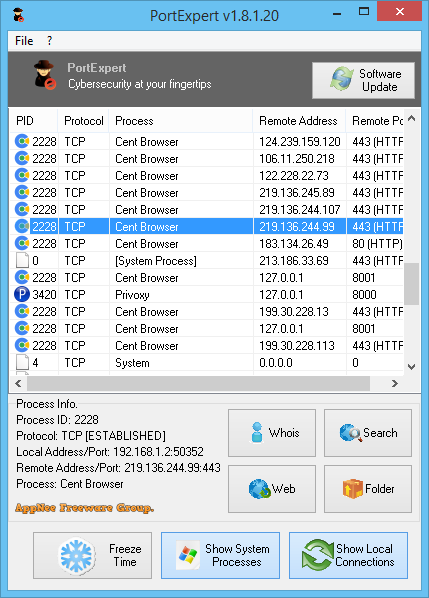
PortExpert is a free system process port monitoring and management tool, developed by KC Softwares from France. Its purpose is simply to monitor any programs connected to the Internet in real time, letting you know which ports and what IP addresses they are connected to. It is essentially equivalent to dynamically executing the "netstat /ano" command in the CMD.
Loading...
Loading...