#4460
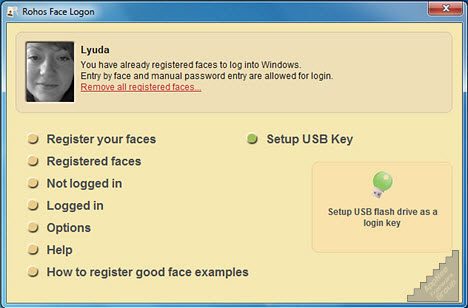
Rohos Face Logon is a facial recognition system based computer login software working well with any Windows-compatible cameras on Windows, developed by SAFEJKA S.R.L. from Moldova. It makes the traditional Windows logon procedure easier, faster and more secure by providing a user identification based on the artificial neural network technology - biometrics verification in an automatic continuous process.
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
#4446
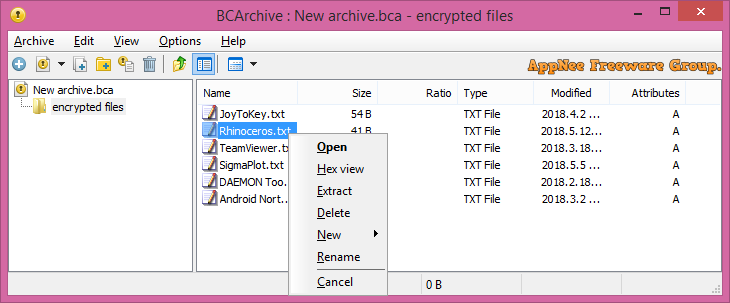
BCArchive is a small, intuitive and easy-to-use file compression & encryption freeware from Finland. With it, you can encrypt and compress a set of files and folders into a single, encrypted and self-extracting archive file with password protection.
Loading...
Loading...
Loading...
#4429
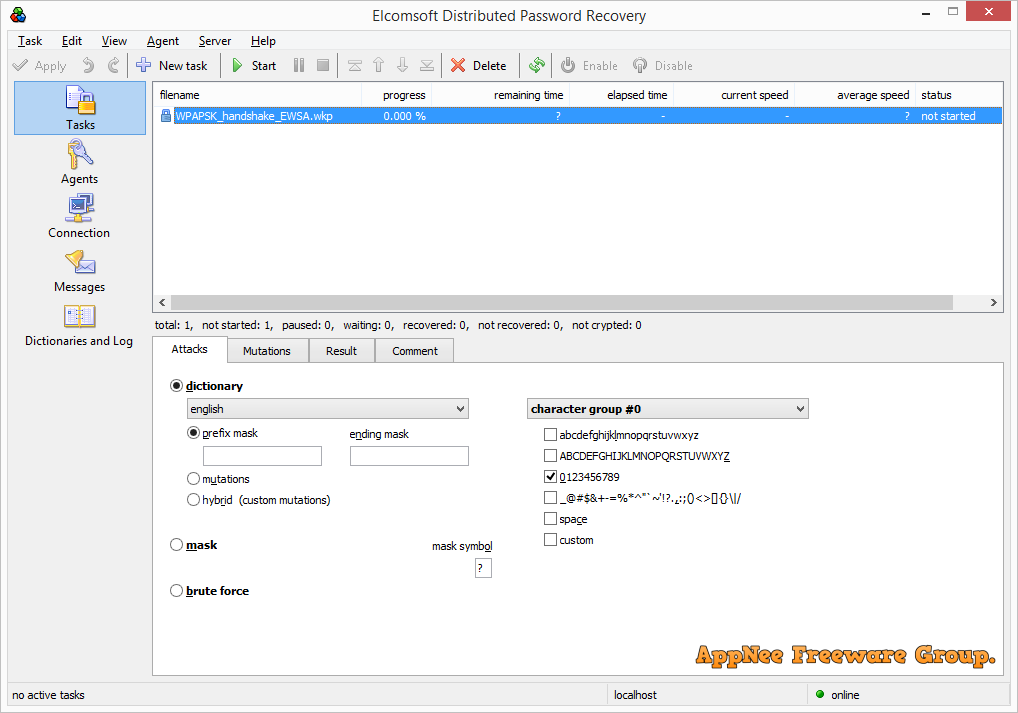
ElcomSoft Distributed Password Recovery is a high-powered and distributed password brute-force cracking tool supporting hardware (GPU) acceleration, developed by ElcomSoft from Russia. It utilizes NVIDIA GPU and/or distributed computer to speed up the calculation so as to realize the speedup of password cracking/recovering. Therefore, it is mainly applied to rapid password recovery/crack, computer forensics, restoring the most complex passwords and strongly encrypted keys within limited time, and some other fields.
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
#4360
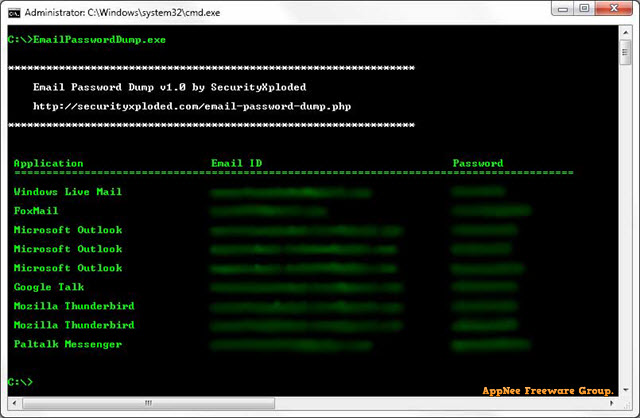
Email Password Dump is lightweight and user-friendly command-line based (working in a DOS window) free application developed by SecurityXploded from India. It's used to quickly discover/recover and then display the email passwords stored in many popular email clients, such as Outlook, Outlook Express, Pidgin, Windows Live Mail, GTalk, Thunderbird, IncrediMail, Foxmail, and more.
Loading...
Loading...
Loading...
#4338

In Windows 10, a wide range of privacy settings involving users' privacy exist throughout the whole system, so that ordinary computer users cannot protect themselves from the so-called data mining behaviors taken by Microsoft. Therefore, we have to turn to third-party applications to protect our privacy when using Windows 10. W10Privacy is one of the most comprehensive software solutions, developed by Bernd Schuster from Germany.
Loading...
Loading...
Loading...
#4293
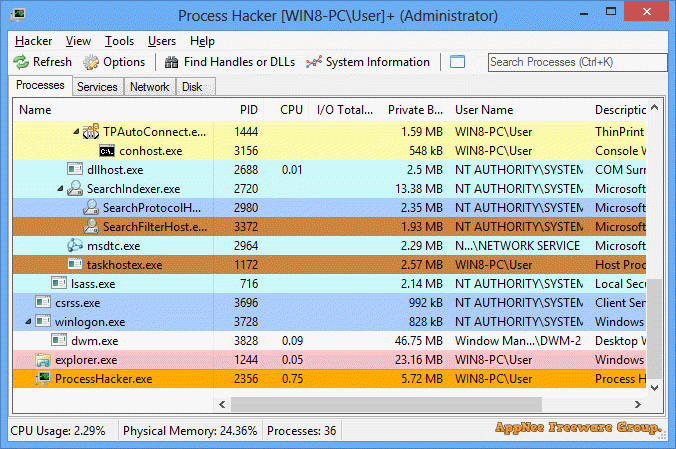
Today's viruses, trojans and many other malicious software are much smarter and more shrewd than ever before. In other words, the traditional methods of identifying suspicious processes such like by checking the startup items have been far from enough. For example, they have been used to embed themselves into system processes, inject into driver files, disguise as system services, and so on, so as to implement autorun and bypass the scanning and killing of most anti-virus software. As a consequence, we could see that more and more antivirus software AIDS came into popular.
Loading...
Loading...
Loading...
Loading...
#4246
To do forensics to a computer, we can use WinHex; whereas to do the same thing for smartphones, you can use the all-in-one and pioneer phone forensics solution in this field - MOBILedit Forensic Express to gather evidence from phones on Windows.
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
#4152
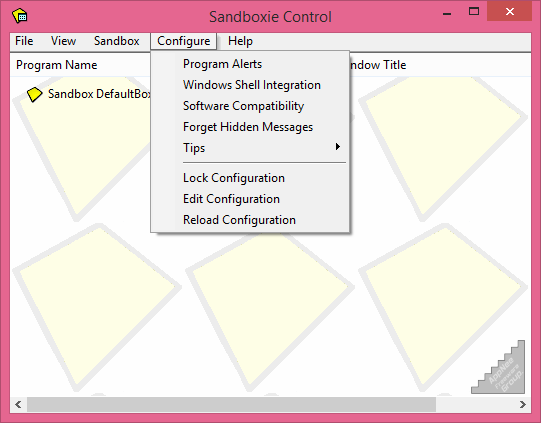
As is known to all, sandbox is a container in which everything can be overturned and restarted. The working principle of Sandboxie is pretty similar - running the browser or other applications in an isolation, virtual "sandbox software environment". This way, any changes or modifications made by these programs can be instantly emptied/eliminated at any time, thus ensuring the safety of operating system and personal information.
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
#4145
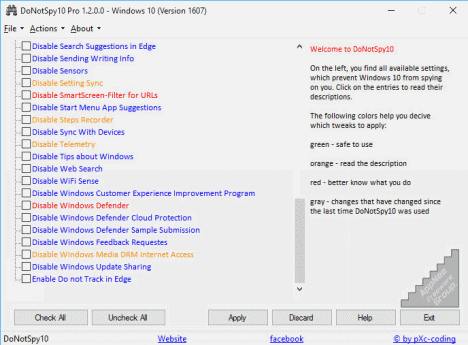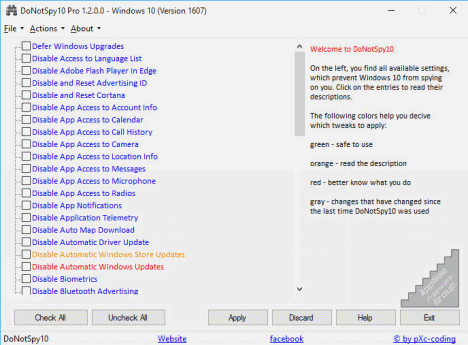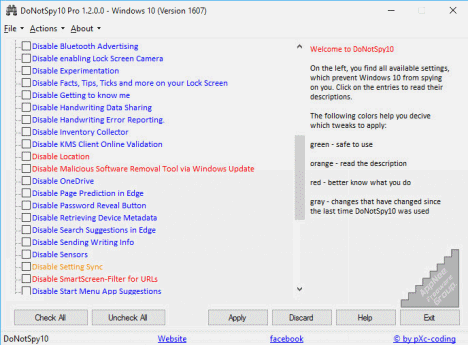
Windows 10 started to blatantly monitor and steal user privacy info, this is a public fact that is daunting for advanced computer users. Because it secretly monitors user behavior and privacy in the background, without notifying the user or getting user's permission. It then uploads the relevant data to Microsoft's official servers, FBI headquarters, and other selling ways. At the same time, this process takes up lots of your network bandwidth. Especially, most of the related settings are hidden and do not allow users to selectively shut down at all.
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
#4059
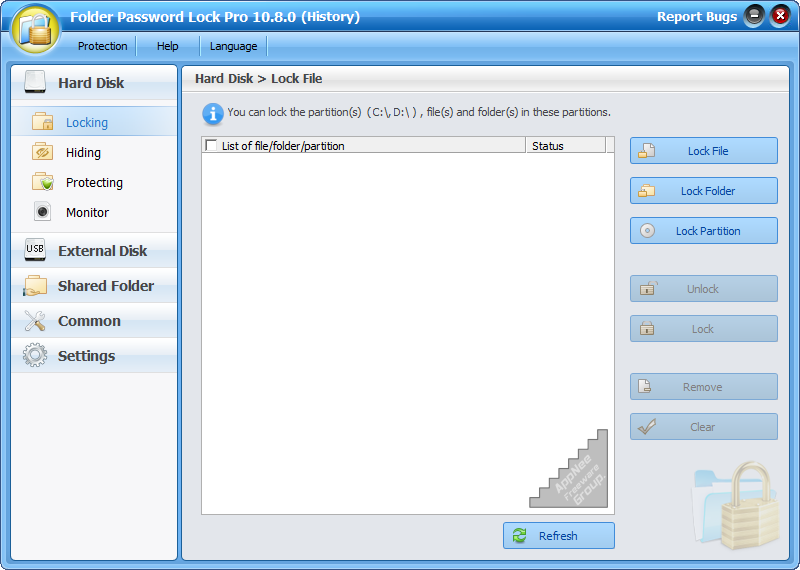
Whether on your own computer or a public one, we always have some important or privacy-related files and data that do not want others to see or get. In this case, what we can do is to use some software to protect them in primarily five ways: monitoring (passive), hiding (junior), locking (can be easily hacked by advanced computer users), password protecting (ditto), encrypting (the safest, but not convenient).
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...