#1774
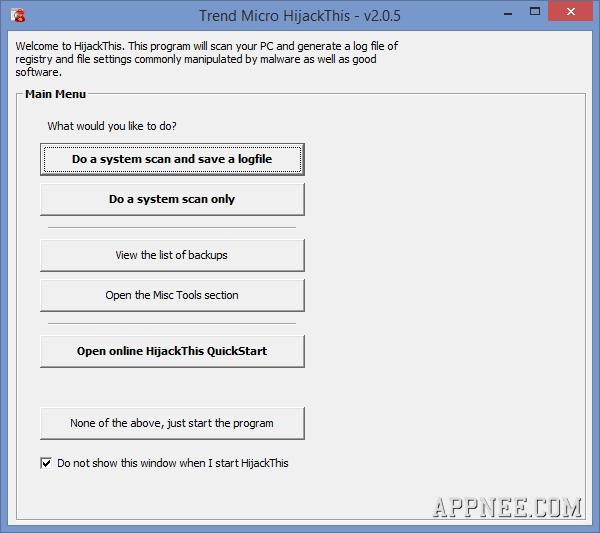
HijackThis (AKA: Trend Micro HijackThis, HJT for short) was once one of the most popular malicious code, virus scanning and fixing utility for advanced PC users. Originally written in Visual Basic by a student named Merijn Bellekom in Netherlands using his spare time. It opened source after acquisition by Trend Micro company in 2007.
Loading...
Loading...
Loading...
Loading...
Loading...
#1430
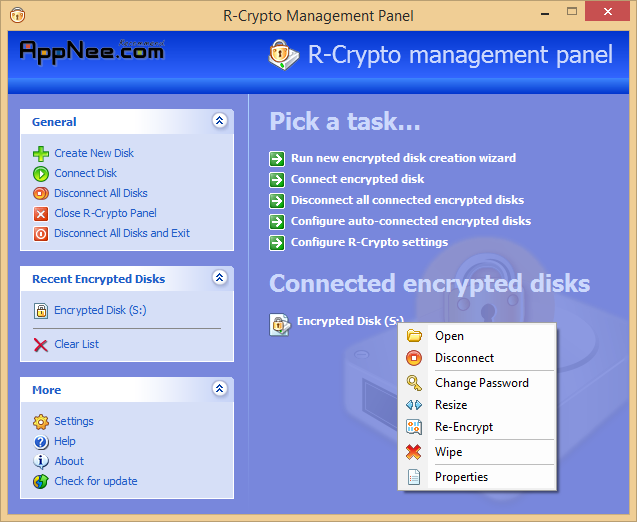
R-Crypto (R-Crypto Disk Security) is a data encryption tool with very outstanding performance, its working principle is to create a password-protected and encrypted virtual disk partition, and then using the real-time encryption and decryption technology to the data files stored in it, after that, only through the correct password to access (supports LAN access).
Loading...
Loading...
Loading...
#1322
Loading...
Loading...
#1155
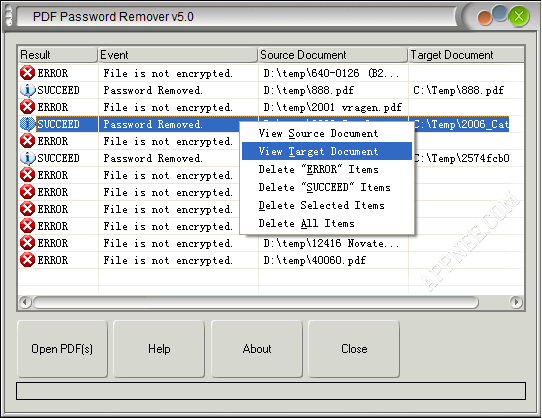
For those PDF files which are protected with password, i.e.: not permitted to edit, change, print, copy, add annotations, etc. At this time, we can turn to VeryPDF PDF Password Remover, with its help we can unlock these limitations easily by removing the password of PDF file.
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
#1128
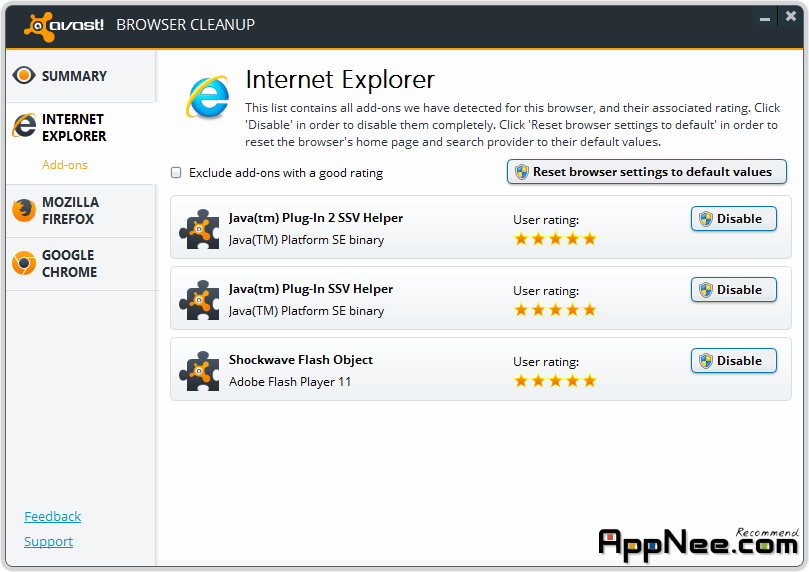
Most of the time, after installation of some kinds of software, our browsers appear to be more and more slow when starting and their interface become more and more bloated.
Loading...
#917
PSMenu (short for Portable Start Menu) is a simple and free start menu application, designed to provide quick programs starting service for your portable devices (USB Flash Disk, mobile HDD, etc.).
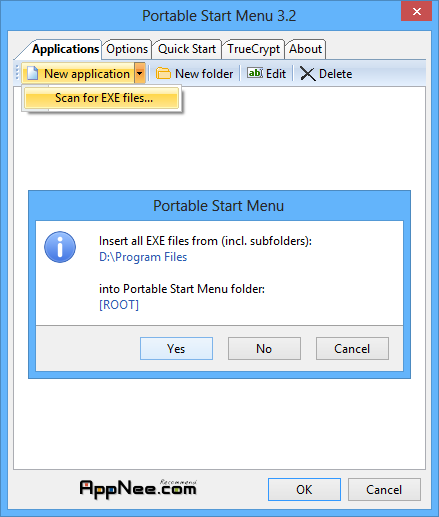
Loading...
Loading...
Loading...
#793
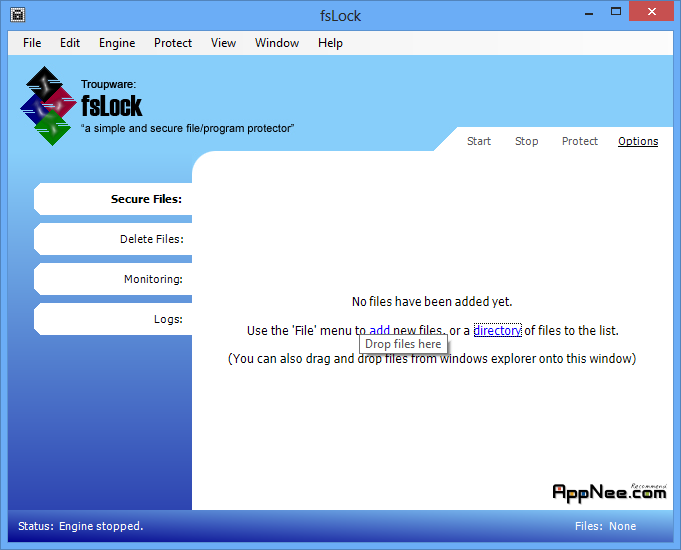
In order to ensure the safety of important files, we often think of the method of encryption, this time we have to mention the famous TrueCrypt. But when using TrueCrypt, we need to specify another file for camouflage, yet this file itself is the same as common file.
Loading...
#772
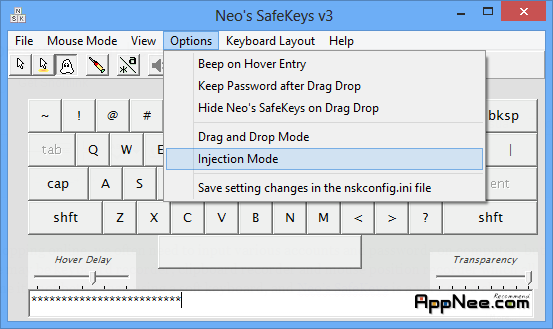
When playing games, surfing the internet or shopping online, we often need to input various accounts and passwords on computer, but if your computer has infected viruses, so there may be keyboard recorder, clipboard recorder and mouse position recorder which all may steal your account information, at this time it's not better than using a soft keyboard, and Neo’s SafeKeys is a very good choice.
Loading...
Loading...
Loading...
#738
It spreads a lot of methods for hiding document into image on the Internet, just in order to achieve the goal of encryption, unfortunately, not only the process is very troublesome, but also it is impossible to realize the encryption of multiple files or folders.
Loading...
Loading...
Loading...
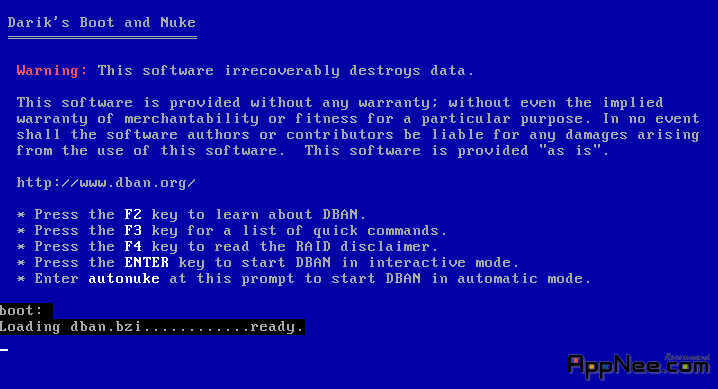
#700
Any PC hard disk used for a long time has innumerable personal data, let alone various commercial computers. These data are mixed, which even has personal confidential files, once outflowed, the consequences will be unimaginable.
Loading...
Loading...
Loading...
Loading...
Loading...