#2326

In 2015, Norton's all security services/products (Norton AntiVirus - NAV, Norton Internet Security - NIS and Norton 360 - N360) have been discontinued by Symantec and replaced with Norton Security (with Backup) with improved performance and superior design. But please note: Norton 2014 can work normally, including the upgrading of virus database.
Loading...
Loading...
Loading...
Loading...
#2315
The Database Hacker's Handbook is another top-quality book after The Shellcoder's Handbook, in which 4 world's top security experts will teach you how to intrude and defend 7 kinds of today's most popular database servers hand by hand. Moreover, you will deeply learn how to use active defense against invasion.

Loading...
Loading...
#2311

The Art of Intrusion: The Real Stories Behind the Exploits of Hackers, Intruders and Deceivers is another bestseller written by Kevin Mitnick, which will lead you to deeply dig into the true story in real life behind hacking cases.
Loading...
Loading...
#2304
The Art of Deception is a bestseller about social engineering with nonprofit nature in 2002, written by the world famous hacker Kevin D. Mitnick who is also one of the headaches for FBI in the history (of course, after released from the federal prison in 2000 he became one of the world's popular computer security experts).

Loading...
Loading...
#2264

Kali Linux is a comprehensive platform for penetration test and security audit, has a wide range of usages in the information security industry. It comes with many advanced tools that can be used to identify the target and detect, exploit the vulnerabilities that have not been discovered in the target network.
Loading...
Loading...
#2214
About Kali Linux, if you previously used or knew about BackTrack Linux series, then I will simply say, Kali is the upgrading product of BackTrack. From Kali, BackTrack will become history.

Loading...
Loading...
#2149
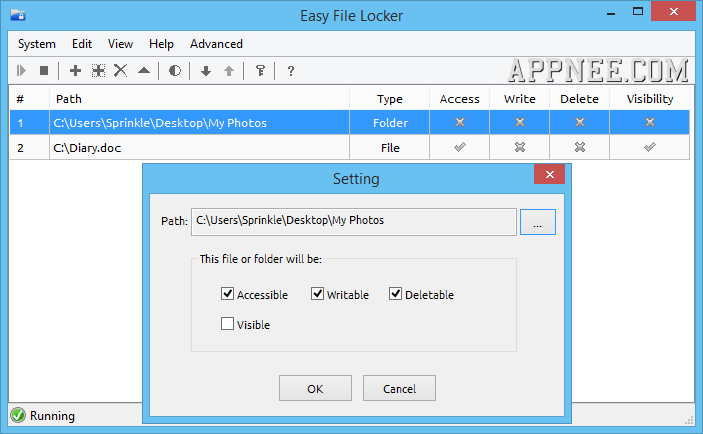
Easy File Locker (EFL for short) is a very compact and user-friendly file/folder all-round protection (locking, hiding, etc.). Any file/folder protected by it will not be able to be accessed, no writing, no deleting, or invisible (hidden). Of course, it provides so high degree of freedom that you can set up protective properties as need.
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
#1920
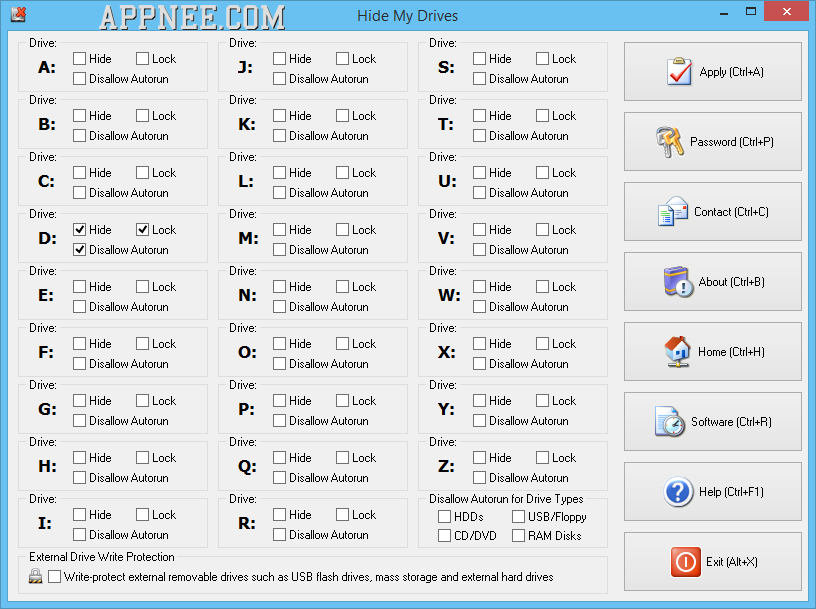
Hide My Drives (formerly called DiskLock) allows to protect any kind of drive (including USB flash drive, Floppy, HDD, SD Card, Mobile HD, CD/DVD, even network or RAM Disk) under Windows, by hiding or locking (password-protect, write-protect). At the same time, it also can disable their AutoRun function.
Loading...
Loading...
Loading...
#1349
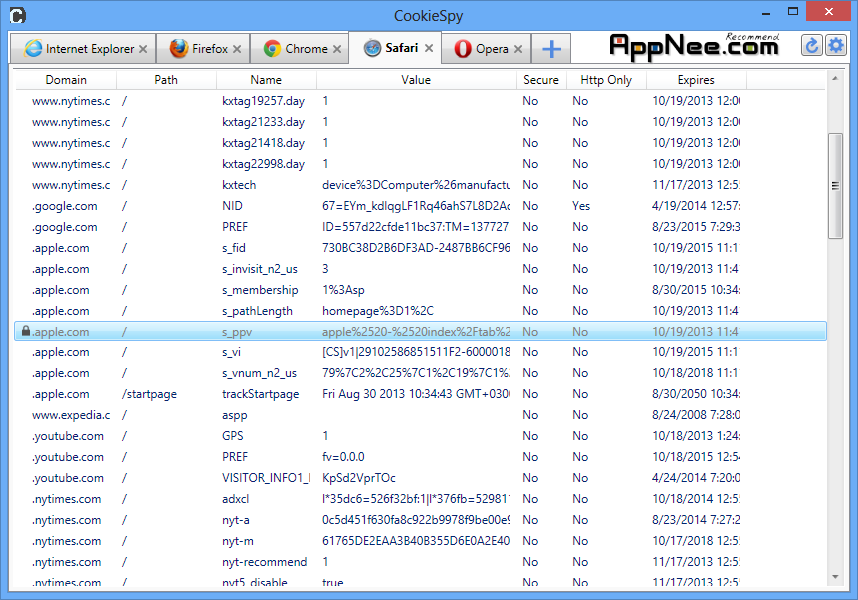
CookieSpy a popular web browser cookies (also known as HTTP cookies, internet cookies, web cookies or simply cookies) viewer and manager, supports all the common browsers.
Loading...
Loading...
Loading...
Loading...
#772
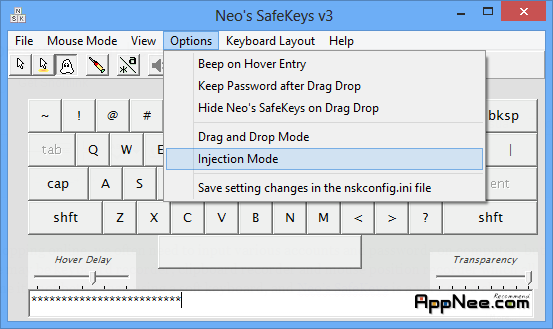
When playing games, surfing the internet or shopping online, we often need to input various accounts and passwords on computer, but if your computer has infected viruses, so there may be keyboard recorder, clipboard recorder and mouse position recorder which all may steal your account information, at this time it's not better than using a soft keyboard, and Neo’s SafeKeys is a very good choice.
Loading...
Loading...
Loading...