#2861

Without any doubt, Wireshark (formerly called Ethereal) is currently the world's most famous, foremost free and open source network packets capture & analysis tool. Its appearance puts an end to the future of all similar business software.
Loading...
Loading...
Loading...
Loading...
#2793
Good, convenient things will always be popular, get more attention from users, and followed by exposing more problems. The wireless network is one of such new things, which began to catch on around the world due to its application on mobile platform.

Loading...
Loading...
#2787

First of all, about the author of this book "Johnny Long", he has begun to research using Google to test the potential safety hazards of websites and computers as early as in 1995. What he does has developed and formed today's Google Hacking Techniques - the Google Hacking Database (GHDB) set up by him has been hosted by Exploits-DB now.
Loading...
#2776
To popularize some boring technology, we have to turn to For Dummies or Head First and such as these series of books. Hacking For Dummies, 4th Edition is not only suitable for beginners who are interested in computer system testing evaluation and IT security, but also has great reference value for network administrators, information security manager/consultant/auditor, and other professionals.

Loading...
Loading...
#2744

Today, wireless network has got very extensive application because of its convenient use and structure, and will eventually cover every corner on the earth, I believe. But due to its broadcast form of data transmission in a wireless network environment, that will inevitably lead to security issues. Of course we can ensure data security by setting different encryption methods in a wireless router, but some loopholes of Wi-Fi network or the router itself can often make every trained hacker be able to crack/hack it.
Loading...
Loading...
Loading...
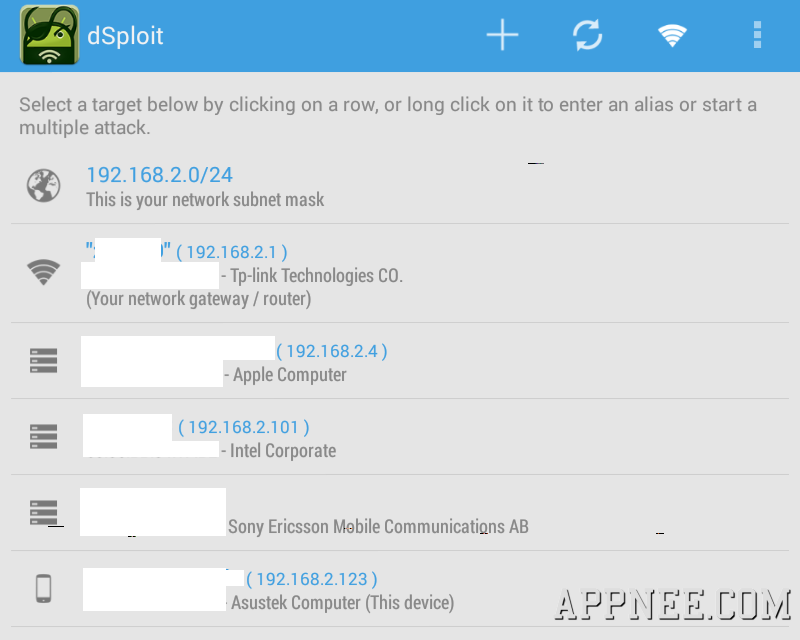
#2612
With the development of mobile devices and network, intelligent mobile phone has become a new paradise for hackers. Imagine, under this environment of everybody holds a smart phone nowadays, nothing is more active than the mobile phone viruses and the vulnerabilities' exploits of software and mobile network. Therefore, to understand and master some practical security tools seems necessary and meaningful.
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
#2525

Kevin Mitnick is referred to as "The world's first-rate hacker", his legendary life and hacking experience have become topic that industry and major news media take delight in talking about. Of course the present Mitnick (gave up evil and returned to good) has become the world's famous white hat hacker, he uses his own experience to guide the well-known enterprises and organizations to enhance their safety and protection measures.
Loading...
#2447
In this post, AppNee will continue to release all kinds of popular, long-tested password dictionaries with very high quality. All of them are proven by users from all over the world, so that any dictionary generated by tools can not be comparable to them. Moreover, they cover all application scopes, fields and uses (we will make the corresponding identification).

Loading...
Loading...
Loading...
Loading...
#2325

Reversing: Secrets of Reverse Engineering described a long-running seesaw battle launched between reversing and anti-reversing. The author reviewed in detail the advantages and shortcomings of every gesture and motion used by both sides for us as a narrater.
Loading...
Loading...
Loading...
#2311
The Art of Intrusion: The Real Stories Behind the Exploits of Hackers, Intruders and Deceivers is another bestseller written by Kevin Mitnick, which will lead you to deeply dig into the true story in real life behind hacking cases.

Loading...
Loading...