#5647
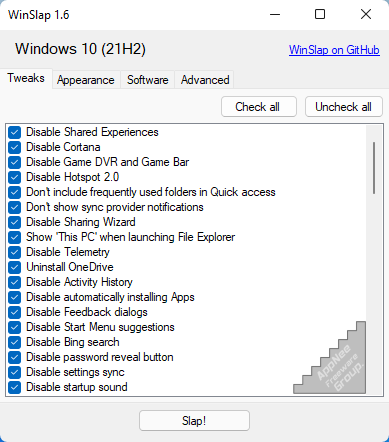
WinSlap is a free and open-source handy tool for quickly configuring a Windows 10 installation with a series of useful tweaks and settings. It was originally developed for personal use only by Sven Mauch from Germany, so there is no guarantee that it works as intended, doesn't break your system or is actively maintained.
Loading...
Loading...
Loading...
Loading...
#5627
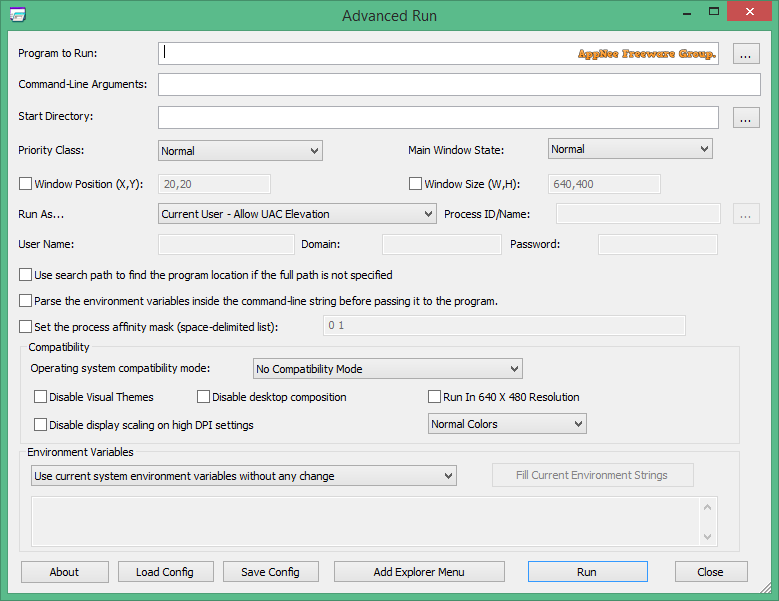
Sometimes we may want a program to run as a window, to be automatically minimized after running, to run multiple instances of a program with different parameters (i.e.: software multi-opening, multi-boxing), or to automatically appear somewhere with a fixed window size after running... These ideas are beautiful, but they are very difficult to implement. But now you can try Advanced Run.
Loading...
Loading...
Loading...
#5613
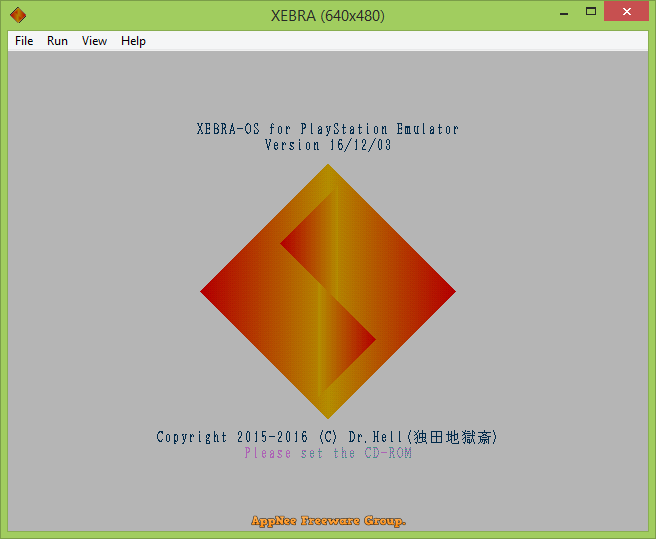
XEBRA is a little-known but excellent free PlayStation emulator for Windows and Android platforms, developed by Dr.Hell from Japan. It strictly focuses on the accuracy of PlayStation emulation, does not use any plugins, and only outputs in native video resolution. At the same time, it is also one of the very few PSX emulators that is compatible with PocketStation.
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
#5612
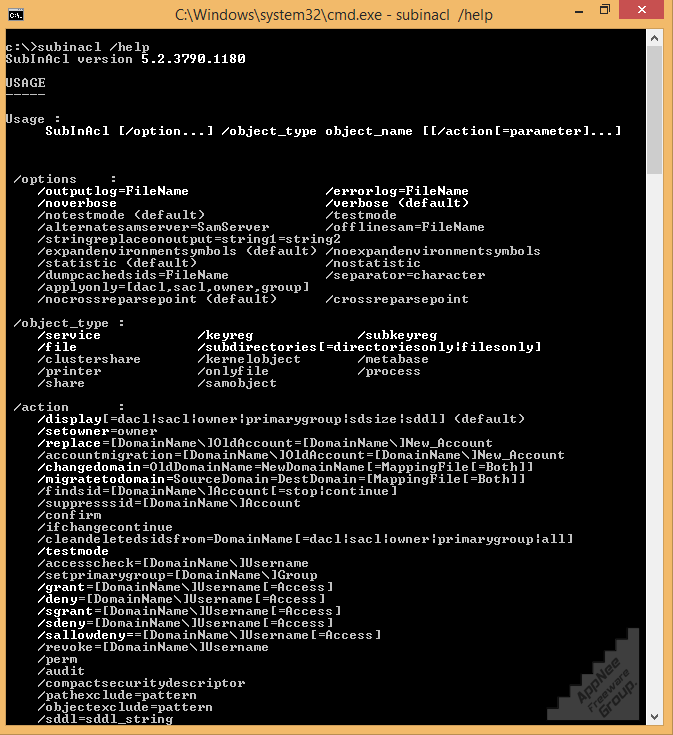
SubInACL is a tiny tool from Microsoft for performing permission management on folders, files, registries, services, and other objects. It was released as one of the tools in Windows Resource Kits. It is very powerful and practical, and much more powerful than cacls and its replacement, icacls. It is considered to be an edge tool for setting access permissions, suitable for professionals such as programmers and administrators.
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
#5567
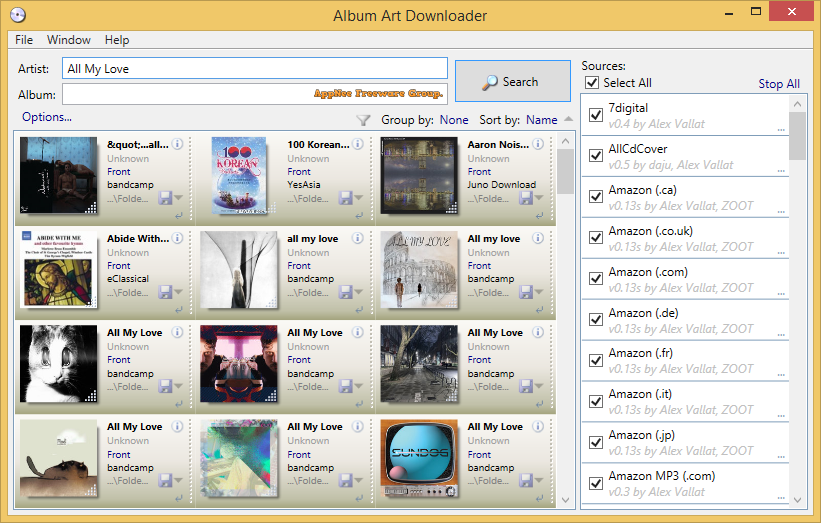
One of the common situations when you get music from the Internet is that there is no album cover in some music files. For music aficionados, this is unbearable. Although some music player programs have built-in features such as tag and album cover fixes, they are still not professional or powerful enough to be considered indispensable.
Loading...
Loading...
#5539
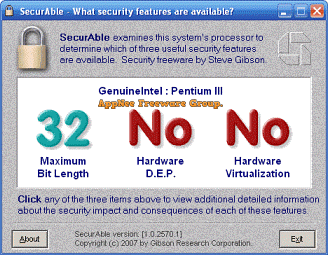
To use the virtualization technologies (such as virtual machine) with certain combinations of some version of Windows and some model of CPU, you need to check to see if your computer supports the hardware level virtualization capabilities. SecurAble is a CPU security features detection tool, can check if your processor chip supports 64-bit, VT (Virtualization Technology), and hardware data execution protection (Hardware D.E.P.) these three state-of-the-art features that are related to the overall security of a system.
Loading...
#5513
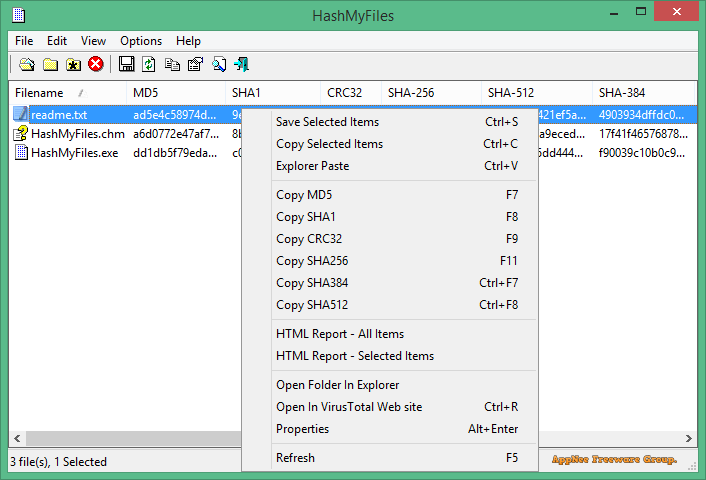
In the process of publishing various types of files on the Internet, whether the document has been tampered with is the main concern of both the publisher and the receiver. That's why message digest algorithms like MD5, CRC32 and SHA-1 are used to calculate and check the unique hash value for files, so as to ensure that the files in circulation remain untouched. This is where utilities like HashMyFiles come in.
Loading...
#5492
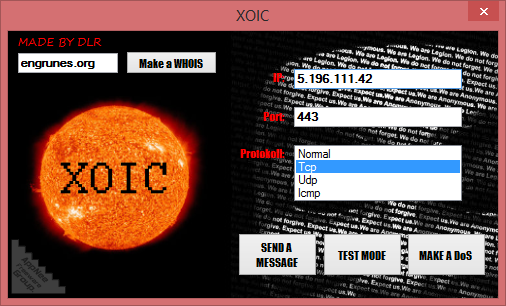
XOIC is another foolproof DoS/DDoS attack launching tool (euphemistically called server stress testing tool) for Windows. It executes (D)DoS attacks to the target IP Address based on the port and protocol selected by user. Its developer claims that XOIC is more powerful than LOIC in many ways.
Loading...
Loading...
Loading...
Loading...
Loading...
#5490
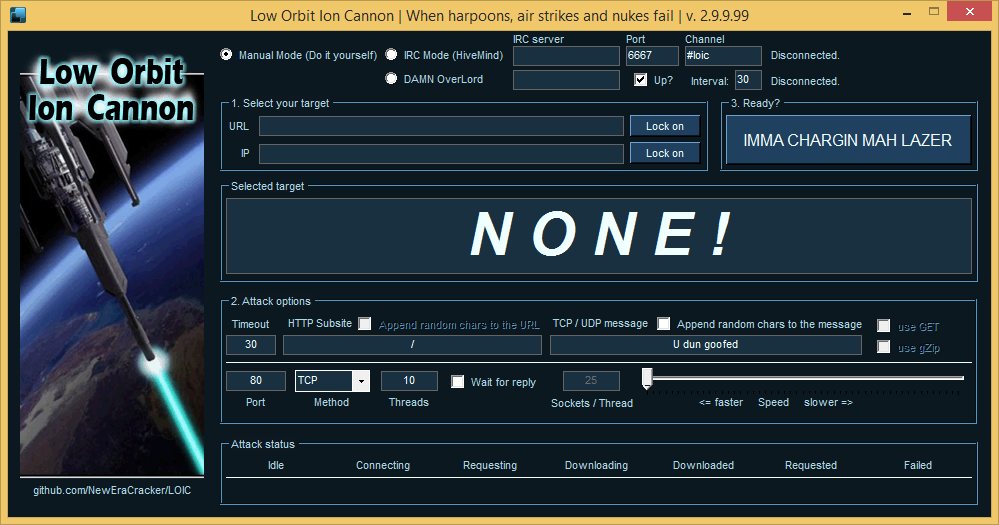
LOIC (short for Low Orbit Ion Cannon) is a free and open-source network/website stress testing tool initially developed by Praetox Technologies (currently maintained by the open source community) with C# in 2014. It's made for educational purposes only (that's to say, you should not use this software for illegal or unethical purposes, including activities that give rise to criminal or civil liability), and intended to help server owners develop a "hacker defense" attitude.
Loading...
Loading...
Loading...
Loading...
Loading...
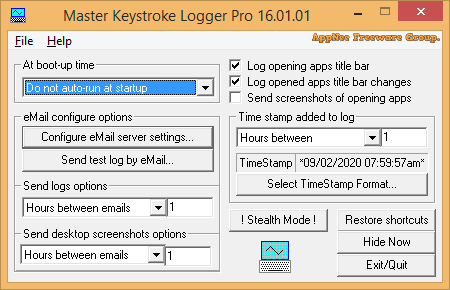
#5438
Master Keystroke Logger is a keyboard keystroke recording program. It has at least two applications: 1) Install it on your own computer, so it lets you know if someone did something on your computer and sends an email notification when you're not there; 2) Install it on someone else's computer as a hidden computer activity monitor.
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...