#7349
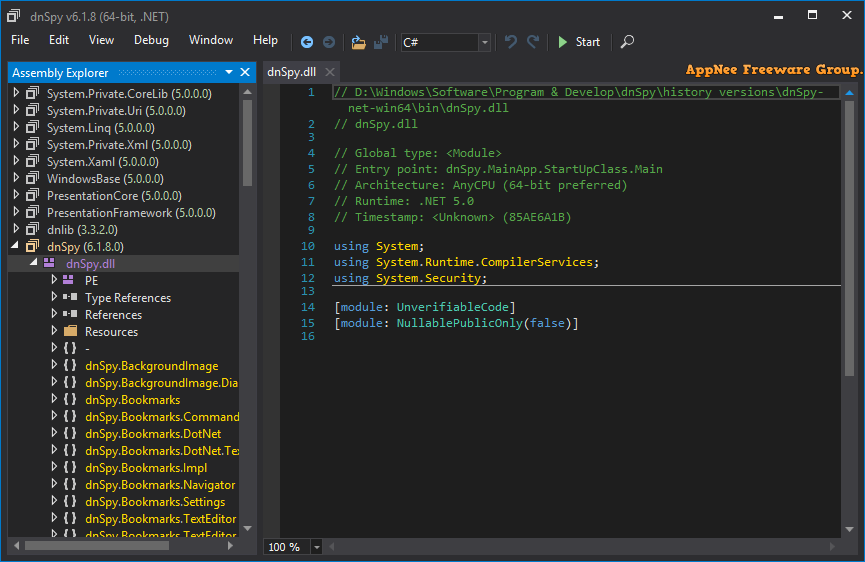
If you are a software developer, you're likely aware that there are times when you need to decompile certain assemblies to gain a clearer understanding of their functionality, that is, to reverse engineer it. However, achieving this without the right tools can often be quite challenging. Fortunately, there are many software solutions available, such as dnSpy, which enable you to obtain quick and effective results.
Loading...
Loading...
Loading...
Loading...
Loading...
#6710
Embedded devices, which are essentially microcomputers of chip size, have become an integral component across various objects they control, including but not limited to phones, automobiles, credit cards, laptops, medical equipment, and even pillars of critical infrastructure. The omnipresence of these devices underscores the importance of comprehending their security landscape.

Loading...
Loading...
Loading...
#6338
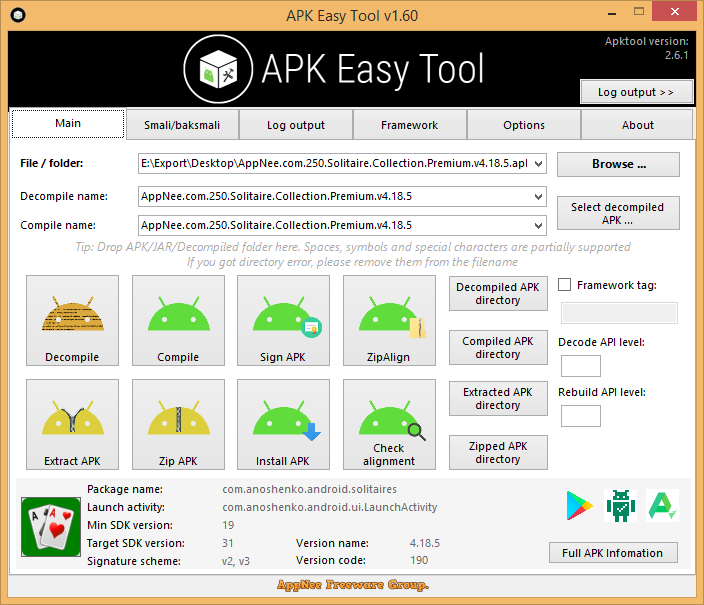
When a novice reverses an Android project, if using Android Killer, some errors often occur during decompilation or recompilation, resulting in the inability to proceed to the next step. Therefore, using some specialized tools is undoubtedly the best choice for novices. Apktool is recognized as an edge tool for APK compilation and decompilation. But its command line interface is not very friendly, so someone specially made a GUI tool for it.
Loading...
Loading...
Loading...
#6047
We all know that APK is actually a compressed file package, so we can extract the files directly from the APK file using the file decompression software like 7-Zip, WinRAR. However, the XML files in the source files obtained in this way are encrypted and cannot be directly viewed. So we need to resort to some specialized APK decompilation tools.

Loading...
Loading...
Loading...
Loading...
Loading...
#5959

Ghidra is a free and open-source software reverse engineering (SRE) framework for Windows, Mac and Linux platforms, developed and maintained by the NSA (National Security Agency) of United States in 2019, written in Java. It is regarded as currently the only thing that can compete with IDA Pro by many security researchers and software developers.
Loading...
Loading...
Loading...
Loading...
Loading...
#5693
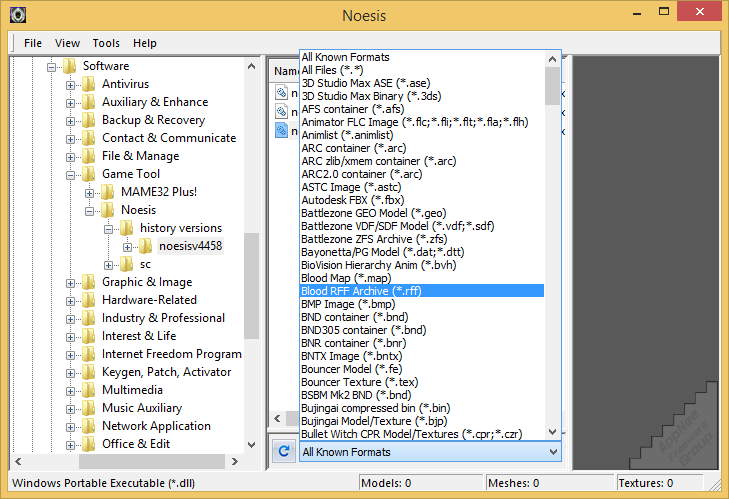
Noesis is a very powerful and easy to use universal game data unpacking tool, created and maintained by Rich Whitehouse. It is mainly used to preview, convert and extract/export (reverse engineer) all kinds of 3D resources/assets from PC and video games, and considered to be one of the must-have tools for making game MODs (Ninja Ripper is another).
Loading...
Loading...
Loading...
#5684
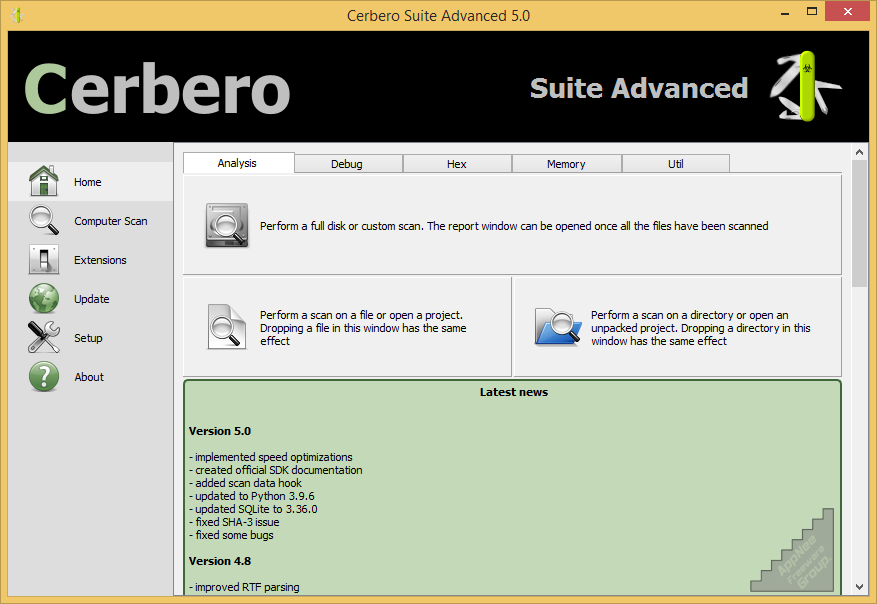
Cerbero is an advanced, professional malware classification and file security analysis tool for Windows, Mac and Linux platforms. It was designed to inspect the structure, code and many other things of dozens of file formats for reversing, malware triage, forensics or software development purpose.
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
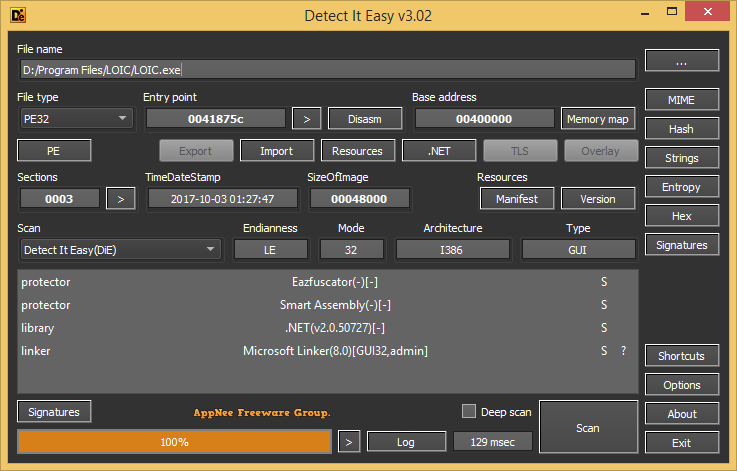
#5604
Packing a program is the most common way developers protect their software. Therefore, in order to crack some software, the first step is to detect whether it has been packed. Detect It Easy (DiE for Short) is a very powerful and easy-to-use PE packers detection tool developed by horsicq from Germany. It has very comprehensive and functional PE packer detection functions, simple operation, and is widely used as one of the most important auxiliary tools for software cracking for now.
Loading...
Loading...
Loading...
#5601

If you are in the software development industry, perhaps a common shareware programmer, or an engineering manager, you need to protect your software. In order to prevent their software from being cracked or illegally used, all software developers will take various measures to protect their software. One of the most commonly used methods is the software registration mechanism.
Loading...
Loading...
Loading...
#5600
In the current Internet environment, most commercial software can be cracked, and that is just a matter of cost and time at most. In order to protect their software from reverse engineering or cracking, almost all software developers use a lot of codes with complex encryption algorithms. That not only costs developers a lot of energy and expense, but also makes the program more chaotic and bloated, and the final effect is not obvious.

Loading...
Loading...
Loading...
Loading...